¹Aakriti Sharma, ²Rashid Hussain
Department of Computer Science and Engineering
Suresh Gyan Vihar University ,Jaipur,India
aakritivashishtha@gmail.com
rashid.hussain@mygyanvihar.
Abstract— Containers have existed for many years, Dockers has not invented anything in this sense, or almost nothing, but it should not be taken away from them, they are at the right time and provide the specific features and tools that are needed today, where portability, scalability, high availability and microservices in distributed applications are increasingly used, and not only that, but they are also better understood by the community of developers and system administrators. Every time less monolithic applications are developed and more based on modules or microservices, which allow a more agile, fast and portable development. Well-known companies like Netflix, Spotify or Google and countless startups use microservices-based architectures in many of the services they offer. Limit and control the resources that the application accesses in the container, they generally use their own file system like UnionFS or variants like AUFS, btrfs, vfs, Overlayfs or Device Mapper which are basically layered file systems. The way to control the resources and capabilities it inherits from the host is through Linux namespaces and cgroups. Those Linux options aren’t new at all, but Docker makes it easy, and the ecosystem around it has made it so widely used. In this paper different level of Docker security is applied and tested over the different platform and measure the security attribute to access the legitimate resource. Additionally, the flexibility, comfort and resource savings of a container that provided by a virtual machine or a physical server is also analysis.
Keywords— Virtualization, Container, Docker, Security, Access Control, Variability, security practices
Introduction
Docker has gained a lot of popularity and usability in business and educational environments, due to the great virtues they possess in terms of deployment facilities and the apparent security options it brings, for being specific applications those that are loaded in the system. However, on the blog, we have not talked much about it and their security features, which in some cases have generated a false feeling that they are systems without any vulnerability and that when displaying the images of the different services required, these will be completely protected against any incident. Docker is a secure and lightweight software container from Docker Inc. that allows you to wrap pieces of software in a file system along with everything you need to run and run one or more applications independently, ensuring that they always run as usual. Same way, regardless of environment or operating system. Docker allows to accelerate the development process, eliminating inconsistencies in environments, improving code distribution and allowing much more effective collaboration between developers. Likewise, Docker, Inc. offers an entire infrastructure in the cloud ( Docker Cloud) that has 24/7 technical support, web administration panel and security for its repositories, as well as an easy and fast way to scale our applications along with other additional services.
Architecture of the Docker repositories:
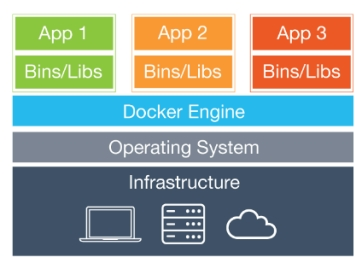
Figure: 01 Docker Architecture
Source: https://www.docker.com/what-docker
However, the Docker repository engine is an open source project that we can download and run locally or on our own servers for free.
- DSS Services in Docker to run Services
The DSS service is triggered when a user uploads an image to a Docker Cloud repository: the service receives the image and breaks it down into its respective components. It then compares it to the Known Vulnerabilities databases ( CVE databases) and finally verifies all the components at a binary
level to validate their content. This process ensures the security of images at a much higher level than other services. Once the scan result is ready, it is sent to the Docker Cloud service graphical interface. When a new vulnerability is reported to the CVE databases, the DSS service activates and checks if there are any images or components with this vulnerability in the repository and sends a report via email to the administrators of the repository. The information presented both in the graphical interface and in the emails contains data about the vulnerabilities and the images that present them.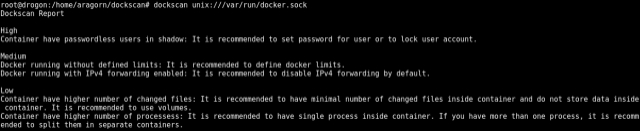
- Docker Security Service operation:
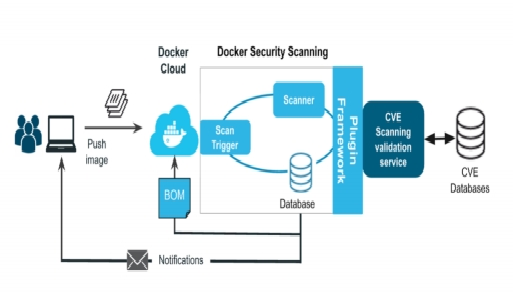
Figure: 02 Docker Security Service operation Flow chart
- Security enhancement in Docker
This new functionality added by the Docker team is really important for the work processes of the development teams that use the Docker Cloud since it will increase the security of the released images and allow their continuous verification. In addition, the DSS service is automatically run by Docker Cloud services, allowing developers to focus on building the product, and having a much more agile and effective workflow.
Docker is an innovative service that allows work teams to focus on development processes through the easy configuration of repositories, where they can have independent environments for their applications, capable of running on any operating system or any cloud platform. . Without a doubt it is a tool that is gaining a lot of strength worldwide, not only within the developer community but also at a business level, since it has already been used by companies as large as: Uber, P&G, Shopify, Spotify, BBC News, among many others. .
In 2017, Sage Dulce during the Black Hat conference, made a presentation called ” How to abuse the Docker API with phantom containers “, wherewith a proof of concept (POC) it demonstrated how in the Docker assemblies on Windows it was possible to use the API through the container’s TCP connections to create or test applications on the running containers.
This action allows an attacker to hide or execute malware in the containers that are operating, generating persistence in the base computer that is very difficult to detect by the PC security mechanisms since they are tools used to affect the container.
This vulnerability has already been corrected by Docker in its updates for the community version and for the Enterprise version, but based on this research, several proofs of concept have been carried out to validate what is stated in the official Docker documents on security (Docker docs ). Here one of the main emphasis is that the security of the container depends on the security of the host and its kernel.
These weaknesses exposed in the investigations are intrinsic to the containers, but very little taken into account when deploying systems in production or even in the integration by host operating systems, such as the one reported in CVE 2018-8115. This takes advantage of the validation of input parameters of a Windows system library just when loading a Docker image.
Because of this, administrators need to use tools to validate some of the risks, mainly validating the relationship between the host and the container, even before executing an image. As seen below, the single Docker daemon may have gaps, due to the way the administrator has configured it.
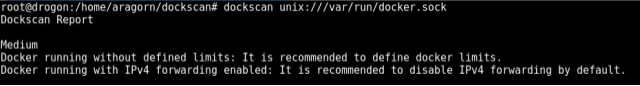
Figure 04: Docker response without containers
Tools like Dockscan allow validating that relationship between the host and the containers, and like every application that is enabled, it can generate risks. In the case of illustration 1, the tool shows the lack of user limits and free traffic between the network of the host and that of the containers. When running a container and exposing some service, new gaps arise that must be taken into account, as can be seen in Figure 4, where the lack of access controls is seen in the container that is marked as a high-risk vulnerability.
There are many Open Source and other paid tools that allow validation of the Docker daemon configuration or the exposed services, such as:
1.Clair Scanner
2.Docker Bench Test
3.OpenScap
4.Docker Notary
5.StackRox
The integration of these or other tools within containerized enterprise DevOps systems such as Docker, incorporate a necessary layer of security for the production implementation of this technology. This layer is increasingly important, generating new tools and methodologies called SecDevOps that seek to have security schemes for production services.
Suppose you work in security. Now the company you work for decides to run some apps using containers, the choice is Docker, after several weeks or months of testing they decide to go into production and someone suddenly says “Should we do a security audit before we go out to production?”, the rest of the film you already know, you and an audit of Docker ahead.All paragraphs must be indented. All paragraphs must be justified, i.e. both left-justified and right-justified. As in any other audit, you can use your arsenal of tools and procedures for applications that work on that infrastructure, analyze file permissions, logs and others. But what about containers, images, and docker files or even the security of orchestration and clustering tools? This article is about that.
Some specific considerations for this audit:
- Check that the images and packages in them are up to date and free of vulnerabilities.
- Automate the audit. We should be able to automate any task. It will save us a lot of time, and we will be able to run such an audit as many times as necessary, forget manual audits unless you are learning.
- Links and volumes between containers. Using base filesystems read-only will make it easier to find problems with the “docker diff” command.
- The bigger the images, the more difficult the audit will be, reduce the images as much as possible.
- The host system kernel is the shared point between all containers running on the same server, the kernel always up to date.
- Comparative Study of existing tools for performing vulnerability discovery and auditing tasks in Docker.
It is possible that some tools have escaped me, so if you know any that are not on this list, I would appreciate it if you could tell us in the comments.
- Docker Bench for Security :
- Description: Docker Bench for Security is a script that checks dozens of standard best practices on deploying Docker in production, which we discussed here in Security By Default in May. All the checks it performs are based on the CIS Docker 1.6 Benchmark document guide .
- Aimed at : mainly the Docker server and some essential tips for images and containers. • Language : Shell script
- Methodology : Run the script on the same Docker server or from a container. You will create a simple on-screen report with INFO, WARN or PASS alerts.
- License : Apache 2.0
- Installation / Usability Level : Easy
- Project Nautilus : presented during the Docker CON 2015 in Barcelona: https://www.youtube.com/watch?v=fLfFFtOHRZQ& the Project Nautilus is a vulnerability scanning and detection service for official repositories in the Docker Hub. In the words of @diogomonica, head of security for Docker Inc., “Nautilus is currently working for all official Docker images.” Nautilus tries to locate any suspicious pieces of software within the images. It does not depend on public vulnerability databases or Linux distributions as other tools do, it uses its own database. We will have more information possibly in the first quarter of 2016 (Thanks Diogo for the information).
- Summary : From the point of view of the Docker server and daemon, it is the best tool to follow Docker configuration and security best practices. I would definitely use this tool along with others that I comment on, as it only covers part of the audit.
- OpenSCAP Container Compliance :
- Description : It is based on the same philosophy as its parent project OpenSCAP , it mainly does a scan by checking CVE databases, and showing the results in reports of various formats, it also supports custom policies . It also provides specific instructions and packages for RedHat 7 as you can see here . Note: SCAP is a North American standard maintained by the National Institute of Standards and Technology (NIST). The OpenSCAP project is a collection of free software tools to help implement this standard.
- Oriented to : Images and containers
- Language : Shell script
- Methodology : run the oscap-docker script against an image or container and we will get a very useful report in html.
- License : GPL v3
- Installation / Usability Level : Easy
- Summary : It is very RedHat / Fedora / CentOS oriented so if you use containers based on these OS, it is highly recommended. If you’re using Atomic , they’ve recently released a new feature that allows you to scan containers using OpenSCAP.
- CoreOS Clair :
- Description: Clair is a container vulnerability analysis service. It works through an API that scans each layer of the container looking for existing vulnerabilities in the Debian, Ubuntu and Centos databases. It can also be used from the command line as we see here . Reports the list of known vulnerabilities that affect each container and can notify users of them. It is used at https://quay.io/
- Oriented to : Images and containers
- Language : Go
- Methodology: By means of API or command, it extracts all the layers of the image and notifies of the vulnerabilities found and stores the information in a database. It also manages its own database that it updates from sources known as CVE.
- License : Apache v2
- Installation / Usability Level : Difficult
- Summary: I have only been able to see the demo and read the documentation, I could not get it to work in CentOS 7.1. I will expand this information as soon as possible.
- Banyan Collector :
- Description: The folks at BanyanOps are the ones who published a report on the large number of vulnerable images that were in the Docker Hub and that was answered in detail by @jpetazzo here . As the authors say “it is a framework for static analysis of Docker images”. Which means it scans more data in addition to vulnerabilities, as seen in their report.
- Oriented to : Images
- Language : Go
- Methodology: Although it can be run from a container, it runs from the command line and connects to a Docker repository that we indicate to do the analysis. See how it works in detail here .
- License : Apache 2.0
- Installation / Usability Level : Medium-Hard
- Summary: It is docker registries oriented, it can be useful for local registries.
- Lynis :
- Description : Lynis is a valid audit and hardening tool for Linux, Mac and Unix, additionally it includes a Dockerfiles analysis module. It also shows some basic Docker server statistics and checks file permissions.
- Aimed at : Dockerfiles
- Language : Shell script
- Methodology : just run Lynis with the docker options and the Dockerfile path in turn and Lynis will analyze some details of said file as installed packages, for example.
- License : GPL v3
- Installation / Usability Level : Easy
- Summary : You could kill two birds with one stone by analyzing the host server and the dockerfiles but I don’t see it very useful at the moment as far as Docker is concerned since the checks it offers are very basic. The author is working on adding more functionality.
- Twistlock :
- Description : In the authors’ words: Twistlock scans container images on docker registries, workstations, or on production servers. Detects and reports vulnerabilities at the Linux distribution level, application framework and even custom client packages. In addition to checking vulnerabilities in public Open Source software databases, they have commercial software feeds. This solution also offers granular control as to actions that users and groups can perform, authentication through LDAP and Kerberos, it has configuration options to control suspicious behavior in containers, roles and malicious actions that may occur, what they call Runtime Defense.
- Oriented to : images, containers and packages. Made for Docker and Kubernetes or Mesos.
- Language : Shell script, Javascript and Go.
- Methodology : Use NIST to check CVEs as well as CIS Docker checks. It does more than simple tests as it has access control, execution level defense, monitoring and continuous integration features.
- License : Commercial based on number of hosts. They have a free developer-oriented edition with a limit of two hosts.
- Installation / Usability Level : Not tested although I have seen how it works live through a demo made by the manufacturer.
- Summary: I have had a session with the manufacturer to see more details of this solution. The truth is that it goes beyond a vulnerability analysis and auditing tool, in addition to this it provides us with a way to manage the security of our container architecture (with Docker, Kubernetes or even Mesos). I think it is the tool that best meets the needs that can be had at the business level. It has a lot of room for improvement, since it is a tool whose version is 1.0.2 but it has a wide list of features and granularity in actions and roles that are very necessary in certain use cases. It is important to highlight, as I have said before, that it is not only a vulnerability management tool, but it goes further.
- Bitnami Stacksmith :
- Description: it is an online tool to generate custom containers via Dockerfiles (in Bitnami’s words: it is a declarative API to generate containers). Although it is not intended to be a security tool as such, it has a functionality that is worth mentioning since it detects and alerts us by screen and email when a container has an outdated or vulnerable component.
- Aimed at: Dockerfiles, images and containers.
- Language : unknown
- Methodology: Use public CVE database https://cve.mitre.org to search CVEs of the components used.
- License : SaaS
- Installation / Usability Level : Easy
- Summary: As a SaaS tool it is very easy to use, from a security point of view, it offers the user a clear and useful view of the status of each container. It is limited to the components they offer in the tool.
- Dockscan
- Description: Like almost all of them, it is a fairly recent tool and in a very initial state, it was launched a few weeks ago, it was presented at BlackHat Europe Arsenal . According to the author: Dockscan is a vulnerability analysis tool for Docker and containers. Reports security issues in Docker installation and container configurations.
- Aimed at: mainly Docker server and some basic tips for images and containers.
- Language : Ruby
- Methodology: use some of the good practices cited in the CIS Docker 1.6 Benchmark best practices. It can work locally and remotely by connecting to a Docker server.
- License : GPL v2
- Installation / Usability Level : Easy
- Summary: Currently it is very limited, although it seems interesting, I would not use it for now, we will see how it evolves, Docker Bench for Security does much more.
- Drydock : (not to be confused with Dry-dock cluster )
- Description: According to the author: drydock is a Docker security audit tool written in Python. It was initially inspired by Docker Bench for Security but tries to provide more flexibility in audits. Drydock allows the creation and use of profiles to reduce false alarms. Generate reports in JSON for easy use. Use the docker-py client to communicate with Docker through the API.
- Aimed at: mainly the Docker server and some basic tips for images and containers.
- Language : Python
- Methodology: Like the previous tool, it uses the CIS Docker 1.6 Benchmark best practices recommendations to check the server configuration.
- License : GPL v2
- Installation / Usability Level : Easy
- Summary: It is still very green, it does some more things than Dockscan but it does not reach what Docker Bench for Security does . We will see how it evolves.
- Batten :
- Description : tool to audit and secure Docker server and containers. It is more or less the same as Drydock or Docker Bench for Security.
- Aimed at : mainly the Docker server and some basic tips for images and containers.
- Language : Go
- Methodology : It runs as a container and checks the server following the CIS Docker 1.6 Benchmark guide.
- License : MIT
- Installation / Usability Level : Easy
- Demo / Presentation : N / A
- Summary : Nothing different than what Drydock or Docker Bench for Security does.
Taking into account that most are tools with less than 6 months of life, But of course there are some that are not worth using for now as it indicate in the comments of some of them. That said, from the point of view of features and business orientation of the application itself Twistlock would be the one that most needs at the moment.
Conclusions
There is a lot of room for improvement and adapting these or other tools to make them really useful at the level of business security analysis. It is not a bad start, at least to test what we have regardless of the state of our environments. It remains to be seen what great players can contribute on this topic and containers (Google, MS, AWS, etc.).In favor of all of them it must be said that it is quite difficult to keep up with Docker since new versions are published with many changes and news almost every week. It imagine that is the price to pay when we work with emerging technologies .In future security in orchestration systems like Kubernetes or even other Docker deployments like AWS ECS.
Acknowledgment
The heading of the Acknowledgment section and the References section must not be numbered.
Causal Productions wishes to acknowledge Michael Shell and other contributors for developing and maintaining the IEEE LaTeX style files which have been used in the preparation of this template. To see the list of contributors, please refer to the top of file IEEETran.cls in the IEEE LaTeX distribution.
References
[1] Boettiger, C. (2015). “An introduction to Docker for reproducible research. ACM SIGOPS Operating Systems Review”, 49(1), 71 -79.
[2.] Felter, W., Ferreira, A., Rajamony, R., & Rubio, J. (2014). An updated performance comparison of virtual machines and linux containers. technology, 28, 32.
[3.] Harji, A. S., Buhr, P. A., & Brecht, T. (2013). Our troubles with Linux Kernel upgrades and why you should care. ACM SIGOPS Operating Systems Review, 47(2), 66-72.
[4.] Scheepers, M. J. (2014). Virtualization and containerization of application infrastructure: A comparison.
[5.] Seo, K.-T., Hwang, H.-S., Moon, I.-Y., Kwon, O.-Y., & Kim, B.-J. (2014). Performance Comparison Analysis of Linux Container and Virtual Machine for Building Cloud.
[6.] Van der Aalst, W., Weijters, T., & Maruster, L. (2004). Workflow mining: Discovering process models from event logs. Knowledge and Data Engineering, IEEE Transactions on, 16(9), 1128-1142.
[7.] Varghese, B., Subba, L. T., Thai, L., & Barker, A. (2016). Container-Based Cloud Virtual Machine Benchmarking. arXiv preprint arXiv:1601.03872.
[8.] Waldspurger, C. A. (2002). Memory resource management in VMware ESX server. ACM SIGOPS Operating Systems Review, 36(SI), 181-194. [14] ACM SIGOPS Operating Systems Review. 36 p.181-194.
[9.] M. Almorsy, J. Grundy, I. Müller, et al. An analysis of the cloud computing security problem. In Proceedings of APSEC 2010 Cloud Workshop, Sydney, Australia, 30th Nov, 2010.
[10.] S. Bellon, R. Koschke, G. Antoniol, J. Krinke, and E. Merlo. Comparison and evaluation of clone detection tools. IEEE Transactions on Software Engineering, 33(9):577–591, 2007
[11.] S. Bugiel, S. Nürnberger, T. Pöppelmann, A.-R. Sadeghi, and T. Schneider. AmazonIA: When elasticity snaps back. In Proceedings of the 18th ACM Conference on Computer and Communications Security, CCS ’11, pages 389–400, New York, NY, USA, 2011. ACM.
[12.] Y. Dang, D. Zhang, S. Ge, C. Chu, Y. Qiu, and T. Xie. Xiao: tuning code clones at hands of engineers in practice. In Proceedings of the 28th Annual Computer Security Applications Conference, pages 369–378. ACM, 2012
[13.] D. A. Fernandes, L. F. Soares, J. V. Gomes, M. M. Freire, and P. R. Inácio. Security issues in cloud environments: a survey. International Journal of Information Security, 13(2):113–170, 2014.
[14.] M. Gabel, J. Yang, Y. Yu, M. Goldszmidt, and Z. Su. Scalable and systematic detection of buggy inconsistencies in source code. In ACM Sigplan Notices, volume 45, pages 175–190. ACM, 2010.
[15.] B. Grobauer, T. Walloschek, and E. Stocker. Understanding cloud computing vulnerabilities. IEEE Security & Privacy, 9(2):50–57, 2011.
[16.] J. Gummaraju, T. Desikan, and Y. Turner. Over 30% of official images in docker hub contain high priority security vulnerabilities. Technical report, BanyanOps, 2015.
[17.] K. Hashizume, D. G. Rosado, E. Fernández-Medina, and E. B. Fernandez. An analysis of security issues for cloud computing. Journal of Internet Services and Applications, 4(1):1, 2013
[18.] K. Hashizume, N. Yoshioka, and E. B. Fernandez. Three misuse patterns for cloud computing.Security engineering for Cloud Computing: approaches and Tools, pages 36–53, 2012.
[19.] Ankit Kumar, Pankaj Dadheech, Vijander Singh, Linesh Raja & Ramesh C. Poonia (2019), “An Enhanced Quantum Key Distribution Protocol for Security Authentication ”, Journal of Discrete Mathematical Sciences and Cryptography, 22:4, 499-507, DOI: 10.1080/09720529.2019.1637154.
[20.] Ankit Kumar, Pankaj Dadheech, Vijander Singh, Ramesh C. Poonia & Linesh Raja (2019), “An Improved Quantum Key Distribution Protocol for Verification”, Journal of Discrete Mathematical Sciences and Cryptography, 22:4, 491-498, DOI: 10.1080/09720529.2019.1637153.
[21.] Ankit Kumar and Madhavi Sinha (2019), “Design and analysis of an improved AODV protocol for black hole and flooding attack in vehicular ad-hoc network (VANET)”, Journal of Discrete Mathematical Sciences and Cryptography, 22:4, 453-463, DOI: 10.1080/09720529.2019.1637151.
[22.] Ankit Kumar & Madhavi Sinha (2019) Design and development of new framework for detection and mitigation of wormhole and black hole attacks in VANET, Journal of Statistics and Management Systems, 22:4, 753-761, DOI: 10.1080/09720510.2019.1609555
[23.] Ankit Kumar, Pankaj Dadheech, Rajani Kumari & Vijander Singh (2019) An enhanced energy efficient routing protocol for VANET using special cross over in genetic algorithm, Journal of Statistics and Management Systems, 22:7, 1349-1364, DOI: 10.1080/09720510.2019.1618519
[24.] Kumar A., Dadheech P., Beniwal M.K., Agarwal B., Patidar P.K. (2020) A Fuzzy Logic-Based Control System for Detection and Mitigation of Blackhole Attack in Vehicular Ad Hoc Network. In: Chaudhary A., Choudhary C., Gupta M., Lal C., Badal T. (eds) Microservices in Big Data Analytics. Springer, Singapore
[25.] Ankit Kumar, Dr. Dinesh Goyal, Mr. Pankaj Dadheech, (2018), “A Novel Framework for Performance Optimization of Routing Protocol in VANET Network”, Journal of Advanced Research in Dynamical & Control Systems, Vol. 10, 02-Special Issue, 2018, pp-2110-2121, ISSN: 1943-023X.
[26.] A. Kumar and M. Sinha (2014), “Overview on vehicular ad hoc network and its security issues,”
