pp.22-26
Udit Yadav1, Akhilesh Pandey2 1Research. Scholar,
Suresh Gyan Vihar University, Jaipur 2Asst. Professor,
Computer Science & Engineering, Suresh Gyan Vihar University, Jaipur
Abstract – In this article the implementation and analysis of image steganographic process is carried out to secure the data on a network. LSB encoding technique is utilized to hide the data in the LSB of 24 bit RGB pixels of colored cover image. The intermediate cover image containing the data (stegano image) shows a good correlation with the original cover image meaning a good amount of hiding of data. If the size of the data file to be sent is more than the capacity of the cover image then multiple copies of cover image are used to embed the data. The correlation of recovered data file with the original data file comes out to be 1 meaning a perfect recovery.
Keywords: LSB, Steganographic, RGB, Data Security
INTRODUCTION
In recent times, the significance of ensuring the network data integrity has been highlighted by the following research works [1–5]. These techniques, while can be useful to ensure the storage correctness without having users possessing data, cannot address all the security threats in network data storage, since they are all focusing on single server scenario and most of them do not consider dynamic data operations. As a complementary approach, researchers have also proposed distributed protocols [6–8] for ensuring storage correctness across multiple servers or peers. Again, none of these distributed schemes is aware of dynamic data operations. As a result, their applicability in network data storage can be drastically limited. Steganography is the art and science of writing hidden messages in such a way that no one apart from the intended recipient knows of the existence of the message [9]. Due to growing need for security of data image steganography is gaining popularity [10]. The main goal of steganography is to communicate securely in a completely undetectable manner [11] and to avoid drawing suspicion to the transmission of a hidden data [12]. This idea of data hiding is not a novelty, it has been used for centuries all across the world under different regimes but to date it is still unknown to most people – is a tool for hiding information so that it does not even appear to exist. However Steganography operates at a more complex level as detection is dependent on recognizing the underlying hidden data. In the presented text the implementation and analysis of image steganographic process is carried out to secure the data on network. LSB encoding technique is utilized to hide the data in the LSB of 24 bit RGB pixels of colored cover image. The intermediate cover image containing the data (stegano image) shows a good correlation
with the original cover image meaning a good amount of hiding of data. If the size of the data file to be sent is more than the capacity of the cover image then multiple copies of cover image are used to embed the data. The correlation of recovered data file with the original data file comes out to be 1, meaning a perfect recovery. Steganography and encryption are both used to make sure data prudence. However the main discrimination among them is that with encryption any person can see that both parties are communicating in secret. Steganography hides the continuation of a clandestine communication and in the best case nobody can see that both parties are communicating in secret. This makes steganography appropriate for a number of responsibilities for which encryption isn’t, such as copyright marking. Adding together encrypted copyright information to a file could be easy to eliminate but embedding it inside the stuffing of the file itself can avoid it being simply recognized and disinterested.
LSB TECHNIQUE FOR HIDING THE DATA
The least significant bit (in other words, the 8th bit) of some or all of the bytes inside an image is changed to a bit of the secret message. Digital images are mainly of two types (i) 24 bit images and (ii) 8 bit images. In 24 bit images we can embed three bits of information in each pixel, one in each LSB position of the three eight bit values for example:
Let us consider a data byte 1 0 1 1 0 1 0 1
Let the RGB component of 3 pixels read from cover image be:
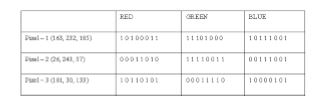
The RGB component of these 3 pixels in the stegano image shall be:
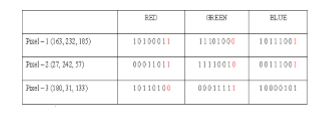
Bits marked red are the bits from data byte (most significant bit to least significant bit) read. Here blue component of every third pixel remains unchanged. In this case, only four bits needed to be changed to insert the character successfully. The resulting changes that are made to the least significant bits are too small to be recognized by the human eye, so the message is effectively hidden. An automated system is designed to upload and download the data to network and from the network, the flow charts for the uploading the data and downloading the data are demonstrated in the Fig.1 and Fig.2 below a) Encoding Process :
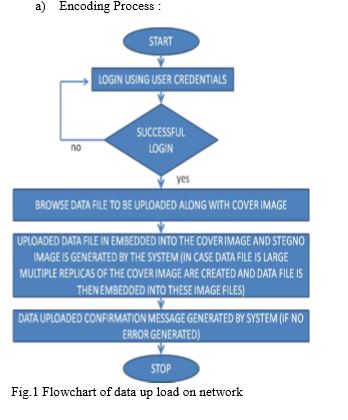
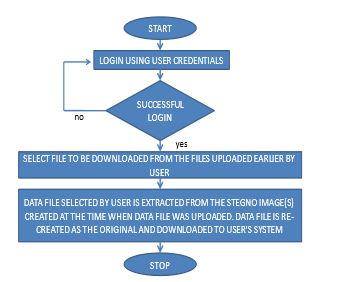
Fig.2 Flowchart of data down load on network
Procedure:



The algorithm used can be summarized as like we consider a cover image Image_1 of size 120*140, i.e. width of image is 120 pixels and height is 140 pixels, and a data file data.txt of size 200KB. Here total number of pixels in the image = 120 * 140 = 16800. In every pixel 3-bits of data can be embedded, one bit at least significant bit of RGB component of pixel, so total data bits that can be embedded in the cover image = 16800 * 3 = 50400 bits or 6300 bytes. Total byte of the data file = 200 * 1024 = 204800 Here number of bytes in the data file is greater than byte that can be accommodated in the cover image. Thus we need multiple copies of the cover image to embed the data file, number of Ceiling (204800 / 6300) = 33. So 33 copies of cover image will be created rather denying the client as size of data file is larger than the number of bytes that can be accommodated in the cover image. Now the data file will also be broken down in 33 small chunks by the process, where first 32 chunks will of size 6300 bytes each and last chunk will be of 3200 bytes (204800 – 6300 * 32). Now iterative process will be called to embed every bit of data file into the 33 copies of the cover image to generate the stegno images which shall then be uploaded over the network. In such way the files having a large size can also be uploaded by parts practically having no limit over the data size to be uploaded. The Fig 3 below shows the process in a sequential manner. The complete process can be summarized as follows:

Fig.3 The process of image steganography
In this article an example is taken in which a text data file is hidden in an image. The text file is having a larger size then the capacity of the cover image so multiple copies of the cover image are created to hide the complete data.
ANALYSIS OF THE DESIGNED SYSTEM
In this section an example is taken in which a text data file is hidden in an image. The text file is having a larger size then the capacity of the cover image so multiple copies of the cover
image are created to hide the complete data. The difference images and stegano images at each and every step are analyzed. The data matrices of each image are produced in order to justify the process results and the graphs are drawn for each image RGB components. The correlation between each stegano image is calculated. The text file size used is having a size of 592 bytes. The cover image taken is having 3x15x21= 945 pixels. To hide one byte of data 9 (3 RGB Pixels) pixels are required so the given image can handle 945/ 9 = 105 bytes of data. According to the capacity of the cover image six replicas of cover image are needed to encrypt the complete date. Six Stegano images will be produced to hide the complete data.
The Stegano image 1 produced is shown in Fig. 5.2 (a). It is the enlarged copy of the actual Stegano image produced. The difference image is also created by taking the difference of the cover image and the Stegano 1 image. The difference image is almost black showing no significant difference in the pixel values of the cover image. This makes the hiding of the data at a good level.

(a) (b) Fig. 4 (a) Stegano Image 1 (b) Difference from cover image Here to estimate the similarity of the cover image with the stegano image the correlation of the RGB component is taken with respective components of each stegano image and the results of the correlation are summarized below: Correlation Coefficient shows amount of similarity between two matrices. Here the calculated value Correlation Coefficients of steganoimages with respect to Cover Image are:
Table 1.

To extend the possibility of mathematical verification of security of the method the entropy of the cover image and the different stegano images are calculated and the percent difference between the entropy of the cover image and stegano images are calculated
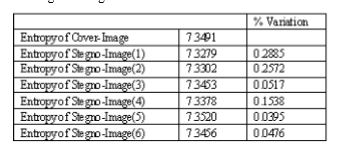
Table 2. Entropy Of Various Stegano Images Compared With The Original Image
From the above table of the entropies it very clear that the difference between entropies the cover image and the respective stegano images is very less also the Percentage of variation in Entropy of Cover-Image and Stegano –images is coming very less that is a very less of fraction showing a good amount matching of the images making the difference delectability very less.
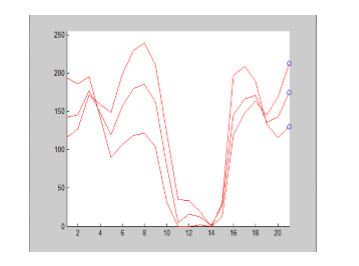
Fig.5 Plot of RGB component of the cover image
CONCLUSIONS
In recent years, the extended growth in server storage provider industry continues to drive the requirements for more and more applications on the servers. These services can be utilized without any investment on bulky IT set up and a large demand to purchase the software. A large pool of the services provided by the serve providing firms without any investment on set up or IT infrastructure no need to hair IT professionals, no need to train the IT resources it is just pay and get the service at a very reasonable rate. The services provided by the servers are so cheap and straight forward but at the same time posses the threat of data insecurity. Because in this the data is available in an remote server, which clients simultaneously is used by several clients at a time in case of theft of the data or any expose of data to any false client knowingly or unknowingly may arise the questions on the data security.
An image steganographic process using the LSB encryption technique is used to secure the data over the networks in such scheme the data to be transferred is hidden in the LSBs of pixels of the cover image so that he data or information to be sent is in the form of LSBs of the cover image which cannot be detected without any prior information of availability of data in that image. The conclusions of the work carried out are summarized below
An automatic system is designed to upload to data on the networks the data as soon as uploaded on the network are encrypted in the LSB,s of a cover image and the data is no longer available as the uploaded format but in the encrypted format now. The data containing capacity of the cover image is finite so if the data exceeds the capacity of the cover image a multiple copies of the cover image are created the data file is broken in the comestible size pieces and assembled back at the time of recovery. An stegano image is created with respect to each cover image embedded with data and the correlation of that stegano image comes out to be 1 in each case, proving that no one can detect the difference in stegano image and cover image. The entropy of each stegano image is having a very less difference with the entropy of the cover image again justifying the a good hiding possibility of data in images.
REFERENCES
[1]. Juels and J. Burton S. Kaliski, “PORs: Proofs of Retrievability for Large Files,” Proc. of CCS ’07, pp. 584–597, 2007.
[2]. H. Shacham and B. Waters, “Compact Proofs of Retrievability,” Proc. of Asiacrypt ’08, Dec. 2008.
[3]. K. D. Bowers, A. Juels, and A. Oprea, “Proofs of Retrievability: Theory and Implementation,” Cryptology ePrint Archive, Report 2008/175, 2008, http://eprint.iacr.org/.
[4]. G. Ateniese, R. Burns, R. Curtmola, J. Herring, L. Kissner, Z. Peterson, and D. Song, “Provable Data Possession at Untrusted Stores,” Proc. Of CCS
