1Rohit Chhabra, 2R R Sinha
1Rohitengineer14@gmail.com, 2drsinhacs@gmail.com,
Associate Professor, Department of Computer Engineering, Suresh Gyan vihar university, Jaipur,Rajasthan India
Abstract: This paper deals with the digital ownership management with the help of Digital watermarking. For inserting any ownership information in any form inside the image or any media like audio video etc, we need a digital watermarking embedding and extraction algorithm, so that owner of the digital object will be able to identify and claim his/her ownership when any illegal person claim his/her false ownership on that object by extracting the watermark. In this research paper, we give a comparison between two watermarking algorithm based on DWT one on additive embedding strategy i.e. ASG algorithm and second one on multiplicative embedding strategy is kedia algorithm. Robustness in term of rotation attack of both the algorithm & tested in terms of PSNR and SNR and compared.
Keywords: DWT, PSNR, SNR, Watermarking, Robustness, Additive embedding, Multiplicative embedding.
I. INTRODUCTION
There is a strong need for security services in order to keep the distribution of digital multimedia work both profitable for the document owner and reliable for the customer. Watermarking technology plays an important role in securing the business as it allows placing an imperceptible mark in the multimedia data to identify the legitimate owner, to track authorized user. Digital watermarking is one of the method to maintain the digital ownership management. There are various ways to embed the watermark by various algorithm here we have taken ASG algorithm as base algorithm and compared this algorithm with the Kedia algorithm. After that we analysis the robustness of kedia algorithm by using rotation attack.
II. PREVIOUS WORK
Sreenivasan [1] had Implemented Digital Watermarking using discrete 2-D wavelet transform and Input image is termarked with a key having Mean = 0 & Variance = 1. This key was generated by utilizing the abstract white Gaussian noise (awgn). Up to my best knowledge this algorithm is available only for embedding the watermark and can be improved for extraction
ASG algorithm [2], also uses Discrete Wavelet Transform (DWT) and additive embedding strategy for embedding and extracting watermark image from the host image. Kedia[11] Algorithm has attempted to bring out the algorithm of ASG [2] in a better way by using multiplicative embedding strategy for watermark embedding and extraction and then analyzing the PSNR and SNR of the extracted watermark with original watermark and between original image and watermarked image without attack.In Proposed algorithm Kedia Algorithm is analysis & comparisons of ASG & Kedia algorithm by rotation attack with SNR & PSNR Values for test the robustness of the algorithm.
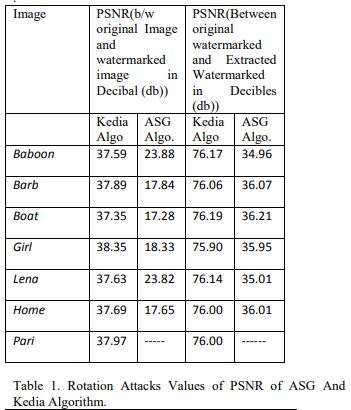
III. RESULT OBTAINED BY KEDIA ALGORITHM
Kedia algorithm imperceptibility evaluated by calculating SNR between original image and watermarked image in Decibels (db), PSNR between original image and watermarked image in Decibels (db), SNR between original watermark and extracted watermark in Decibels(db), PSNR between original watermark and extracted watermark in Decibels(db). Signal-to-noise ratio (often abbreviated SNR or S/N): It is defined as the ratio of signal power to the noise power. A ratio higher than 1:1 indicates more signal than noise.
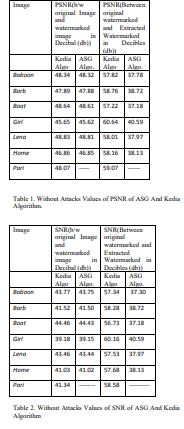
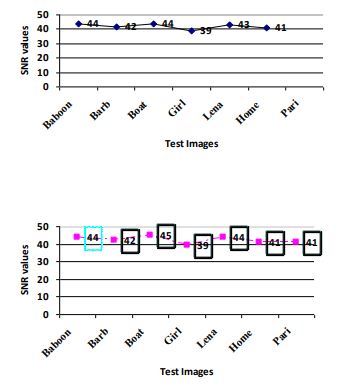
Figure 1. Upper graph shows SNR values between original image and watermarked image for ASG Algorithm and lower graph SNR values between original image and watermarked image for Kedia Algorithm.
Figure 1 shows SNR for various test images show that ratio of SNR is greater than 1:1 ratio for all test images; it means that the value of the signal is greater than the noise.
Noise is the difference between the original image and watermarked image, this difference will show the strength of watermark signal that obscure the original image, least the value of this watermark signal lessen the amount of obscuring the original image i.e. more value of SNR will shows that there is less amount damage in original image. For both the Kedia algorithm and ASG algorithm simulation result shows that the value of SNR is between 39 to 45 that shows degradation in original test image by the watermark signal is very less.
More value of SNR will show less amount of damage in extracted watermark. For both the Kedia algorithm and ASG algorithm simulation result shows that the value of SNR is between 37 to 60 that shows extracted watermark image degradation is very less after extraction process.
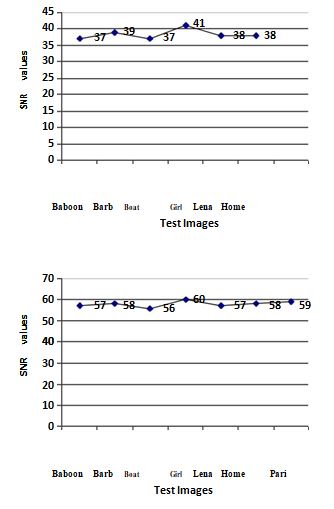
Figure 2 Upper Graph showing SNR values between original and extracted watermark by ASG algorithm and Lower graph by Kedia algorithm.
A. SNR Result Conclusion
(i)The amount of original data presence in watermarked image is more than the background noise. i.e. extracted watermark is recognizable for identity proof.
(ii)Kedia algorithm has higher values of SNR so that we can say that Kedia algorithm has more value of original signal i.e. more matching of the extracted watermark with original watermark so it is better than ASG algorithm.
(iii)Peak signal-to-noise ratio, often abbreviated PSNR, is an engineering term for the ratio between the maximum possible power of a signal and the power of corrupting noise that affects the fidelity of its representation. Because many signals have a very wide dynamic, PSNR is usually expressed in terms of the logarithmic decibel scale [3].
As a measure of quality of reconstruction of lossy compression codecs (e.g., for image compression) PSNR is used. The signal in this case is the original data, and the noise is the error introduced by compression. When comparing compression codecs it is used as an approximation to human perception of reconstruction quality, therefore in some cases one reconstruction may appear to be closer to the original than another, even though it has a lower PSNR (a higher PSNR would normally indicate that the reconstruction is of higher quality). One has to be extremely careful with the range of validity of this metric; it is only conclusively valid when it is used to compare results from the same codec (or codec type) and same content [3]. Typical values for the PSNR in lossy image and video compression are between 20 and 50 dB [3]
IV. RESULT OBTAINED BY PROPOSED ALGORITHM
During transmission and even after reception of watermarked image due to some impairments like introduction of Noise, Image Cropping, Resizing, image get blur and dither, diluted as well as erode which change the position of watermark , sometimes destroy watermark .which is undesirable for owners of image so it become necessary to analyze robustness of watermarking algorithm [4].
![]()
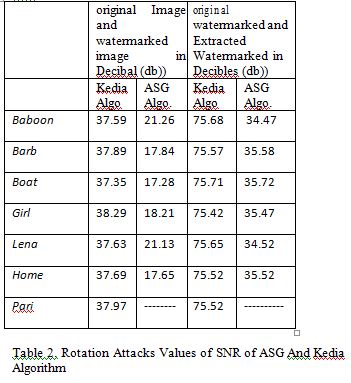
value of SNR for various test images between watermarked image and watermarked image after attack is 18.90 which mean that the quality of the watermarked image is degraded by the attack to a very little extent as the average value of SNR is 42.19 without attack.
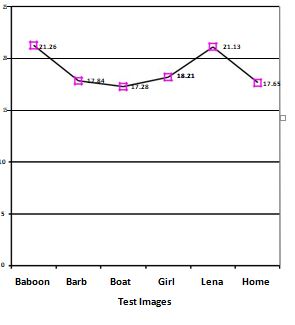
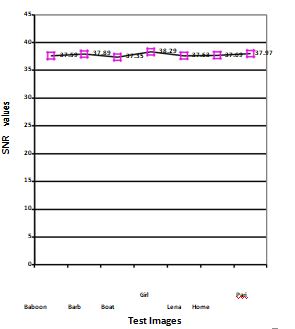
Figure 3 upper Graph showing SNR values between original image and watermarked image after Rotation Attack by ASG algorithm and under graph by Kedia algorithm.
B. SNR Result Conclusion with rotation attack
(i)Watermarked image withstand the rotation attack by both the algorithm. (ii)Kedia algorithm SNR values is far better than the ASG algorithm so watermarked image withstand strongly rotation attack when it is watermarked by Kedia algorithm. SNR values between original watermark image and extracted watermark image after rotation attack are plotted in Figure 4.for various test images.
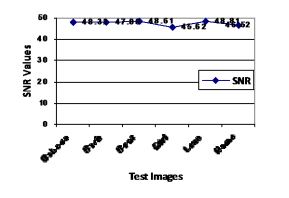
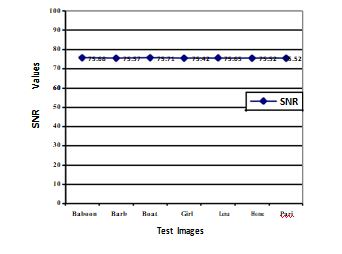
Figure 4 LUpper Graph showing SNR values between original watermark and extracted watermark after Rotation Attack by ASG algorithm and under graph by Kedia algorithm for various test images
C. SNR Result Conclusion of Extracted Watermark with rotation attack
(i)Extracted watermark withstand the rotation attack when watermarked by both the algorithm.
(iii)Value of SNR by Kedia algorithm is far better than ASG algorithm so Kedia algorithm is better withstand the rotation attack.
PSNR values between watermarked image and rotated watermarked image after rotation attack are plotted in Figure 7 Left Graph showing PSNR values between Original Watermark and Extracted watermark image after Rotation Attack by ASG algorithm and right graph by Kedia algorithm.
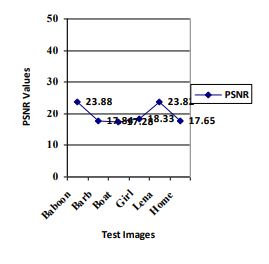
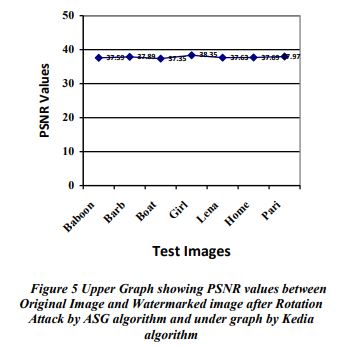
D. PSNR Result Conclusion of with rotation attack
(i)Watermarked image withstand the rotation attack when embedded by both image.
(ii)Value of PSNR by Kedia algorithm is far better than ASG algorithm so Kedia algorithm is better withstand the rotation attack. PSNR values between original watermark image and extracted watermark image after rotation attack are plotted in Figure 8 for various test images.
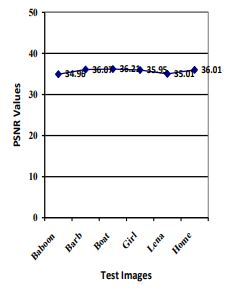
Figure 6. Left Graph showing PSNR values between original watermark image and Extracted watermark image after Rotation Attack by ASG algorithm and right graph by Kedia algorithm.
E. PSNR Result Conclusion of Extracted Watermark with rotation attack
(i)Extracted Watermarked image withstand the rotation attack when embedded by both image.
(ii)Value of PSNR by Kedia algorithm is far better than ASG algorithm so Kedia algorithm is better to withstand the
rotation attack.
V. CONCLUSION
After attacking the Kedia algorithm with Rotational attack and then comparing the PSNR and SNR values with ASG
algorithm we found that the Kedia algorithm is far better than the ASG algorithm as we get more values of PSNR and SNR between original watermark and extracted watermark after attack than the ASG algorithm. Similarly we get more values of the PSNR and SNR between original image and watermarked image after attack than ASG algorithm. Also we can say that Kedia algorithm is robust for the rotational attack and imperceptible
VI. REFERENCES
The heading of the References section must not be numbered. All reference items must be in 8 pt font. Please use Regular and Italic styles to distinguish different fields as shown in the References section. Number the reference items consecutively in square brackets (e.g. [1]).
- Abhijith Sreenivasan (2007 1 Feb), Simple Watermarking using Wavelet transform, (1st ed), [Online]Availiable:http://www.mathworks.com/matlabcentral/fileexcha nge/13834-simple-water-marking-using-wavelet-transform.
- ASG, “Non blind Discreet Wavelet Transformation based Digital Watermark Embedding and Extraction Algorithm”, Master Thesis, Dept. of Comp. Science and Information Technology, Rajasthan Technical University, Kota, Rajasthan, India, 2012.
- Wikipedia, Peak Signal to Noise Ratio (44 ed.) [Online] Available: http: // en. wikipedia. org /wiki/Peak_signal-to-noise_ratio.
- Navnidhi Chaturvedi, Dr.S.J.Basha ,“ Analysis of Image Water marking by DWT and Performance Under Attacks” International Journal of Computer Technology and Electronics Engineering (IJCTEE) Volume 2, Issue 3, June 2012
- “Digital watermarking a technology overview” Hebah H.O. Nasereddin,IJRRAS 6 (1) , January 2011
- Digital Watermarking Techniques: Literature Review
- http://www.digitavid.net/VirtualUniversity/Presentations/ImagingWatermarking.pdf
- Ingemer J.Cox, Joe Killan, Tom Leighton and Talal G. Shamoon, “Secure spread spectrum watermarking for multimedia”, IEEE proceeding International Conference on Image Processing, vol.6, pp 1673-1687 Santa Barbara, California, USA, October 1997.
- George Voyatzis and loannis Pitas, “Application of toral automorphisms in image watermarking”, IEEE proceeding of International Conference on Image processing, vol. 2, pp 237-240, Lausanne, Switzerland, September 1996. IEEE press.
- Thesis on Digital Watermarking in the Wavelet Transform Domain by Peter Meerwald 11, January 2001.
- Naveen Kumar Kedia,Saroj Hirenwal,” Non Blind Digital Watermarking using 2D- DWT,June 2013”, International Journal of Emerging Technology and Advanced Engineering, Volume 3, Issue 6.
