pp.42-48
Krishna Kumar Bohra1, Prof (Dr) Priyadarshi Patni2
Faculty of Computer Science
Lachoo Memorial College of Science and Technology (Autonomous)
Jodhpur, India
saytokrish@gmail.com, pdarshi@gmail.com
Abstract—
The application of MATLab code is used to explain how the LSB substitution is working in inserting a watermark. In an RGB image how the RGB data are stored is explained to understand the substitution by the LSB technique for creating a watermark in the cover image. The image of the watermark and the cover image both are in RGB format but watermark image was converted into binary format to facilitate the insertion of the RGB watermark into the cover image.
Index Terms— Digital Watermarking, Least Significant Bit, embedding RGB, authorization, image formats, lossless compression, spatial representation
I. INTRODUCTION
In this online era image transmission is very common. And it is necessary to care of security issues over web. Watermarking technology is safe and secure method. Watermarking algorithms and encryption of data is basic motive of this paper for image To defend the owner’s right over multimedia object digital watermarking is used to insert watermark. Watermarking can be visible or invisible. The main image in which the watermark is embedded is known as cover image since it covers the watermark. security using RGB watermark in RGB images. Embedding of imperceptible data with maintained image quality is Digital watermarking. The basic purpose of watermarking is to protect ownership and authentication.
Cimg + Wimg = WMimg
The digital image watermarking system essentially consists of a watermark embedding code and a watermark extractor code. The embedding code inserts a watermark onto the cover image (Cimg) and the watermark detector detects the presence of watermark. To understand process of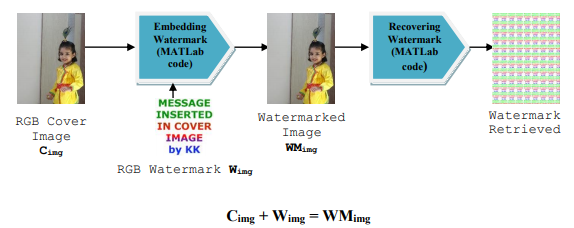
watermarking it is must to understand representation of different types of images in spatial domain.
II. DIFFERENT IMAGE FORMATS
It means the image is made up of finite collection of pixel with finite value from finite set, as shown in figure.

Now the value specified by function is dependent on type of image we are working for. There are broadly 3 types of images in digital computer depending on range of pixel values.
II. REPRESENTATION OF AN IMAGE IN MATLab
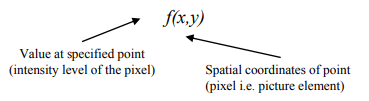
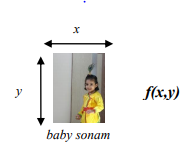
Image in MATLab is stored as a 2 dimensional matrix where each element of the matrix represents the intensity of color of that particular pixel. For a binary image, the value of each element of the matrix is either An image is a 2 dimensional array of points each associated with a value. It can be represented as a function f(x,y) where,
0 <= x >= h
0 <= y >= l
h
i_min <= f(x,y) >= i_max
1. Binary Image (Pixel value either 0 or 1)
2. Grayscale Image (Pixel value range in between 0 to 255)
3. Color Image (Pixel value are made up of 3 sub units range in between 0 to 255)
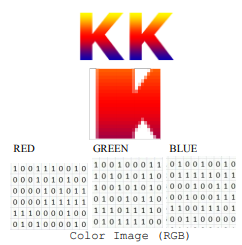
0 or 1 and for a grayscale image each value is in between 0 and 255. A color image is stored as an RxCxT matrix where each element is the RGB value of that particular pixel. As shown in above image.
In MATLab there is set of functions are available named as Image Processing Toolbox™. Which has four basic types of images? MATLab interprets data matrix elements as pixel intensity values. Here are those formats Binary (Also known as a bilevel image), Indexed(Also known as a pseudocolor image), Grayscale (Also known as an intensity, gray scale, or gray level image), Truecolor(Also known as an RGB image).
III. IMAGE FILTERING IN SPATIAL RESOLUTION DOMAIN
The process of modifying or enhancing an image is filtering. The surrounding pixels value is determined by certain algorithm using one pixel. A pixel’s surrounding are also some set of pixels, defined by their locations relative to that pixel.While generating or constructing digital image we have to use pixel and the number of pixels that are referred called spatial resolution. More the number of pixels, higher the resolution and less the number of pixels, lower the resolution. It means spatial resolution refers to clarity, so for different devices, different measure has been made to measure it. For example dot per inch (dpi), lines per inch (lpi), pixel per inch (ppi). And when domain is concern with respect to Spatial domain and transform domain are two approaches for embedding watermarking. Spatial domain watermarks insert data in the cover image changing pixels values or image characteristics. These watermarks have been used for document authentication and tamper detection. The most used spatial domain method is LSB. The aggregate of pixels composing an image is called Spatial Domain. In spatial domain technique the watermark in directly embedded in the pixel values. The detection of the watermark can be done in comparison to original image and watermarked image during the extraction process. The spatial domain process can be denoted by
WMimg(x,y)=Opr[Cimg(x,y)]
Here PImg is processed image, and f is input image with collection of image coordinates and Opr is operator on f The mainly used algorithm in spatial domain is LSB.
IV. LSB (LEAST SIGNIFICANT BIT)
The Least Significant Bit (LSB) is the simplest algorithm in the spatial domain. In the digital image processing, Information can be inserted into every bit of image information. An example of the less perceptible is Least Significant Bit insertion. During insertion each 8-bit pixel’s least significant bit is overwritten with a bit from the watermark. When data is encoded in only the last significant bit of RED color component it should not to be detectable. The human retina has viewing limitations. In our method the least significant bit of each pixel will be used for embedding watermark. If the pixel value is 148 which is 10010010 in binary and the watermark bit is 1 then the value of the pixel will be 10010011 in binary which is 147 in decimal. The cover image consists of a matrix of color and intensity values. And on other side gray scale image, 8 bits/pixel are used. In the least significant bit plane of the cover image
this technique embeds bits of the message after converting intensity value to 0 and 1.However, there is a significant trade-off between the simplicity and robustness, tamper resistance, and other security issues.
The image is likely to be distorted because of scaling, rotation, cropping or lossy compression to the image.
V. EMBEDDING WATERMARKING USING LEAST SIGNIFICANT BIT SUBSTITUTION
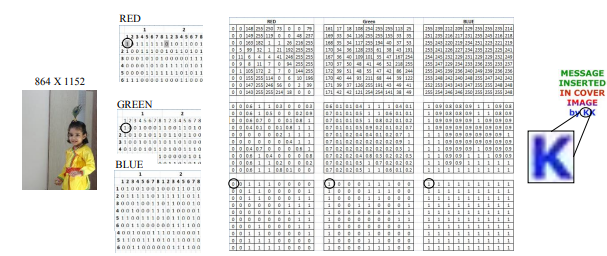
Embedding watermark is the process of hiding the watermark in cover image. Hiding Algorithm:
Step 1 Read message/watermark image file (RGB) using imread() function.[Returns three 2d array containing the image data]
Step 2 Read cover image file (RGB) using imread() function.[Returns three 2d array containing the image data]
Step 3 Calculate sizes of message/watermark object. [Mm/w = Height of Image, Nm/w =Width of Image]
Step 4 Calculate sizes of cover object.[Mc/wkd = Height of Image, Nc/wkd = Width of Image]
Step 5 Normalization message /watermark by dividing value of each cell by 256 of each matrix (R, G and B) and round it.
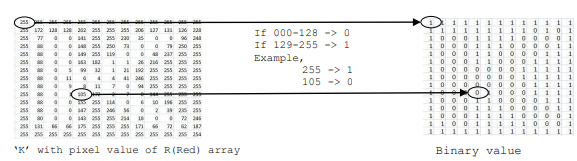
information may require a process of conversion of grey image into binary and then replacing bit into LSB of each pixel value of Red Matrix and so on. [0-128 treated as 0 and 129-255 treated as 1]
Step 6 Store first pixel value of watermark to least significant bit of 8 bits of all the matrixes of cover image corresponding to R, G and B. Step 7 Adjustment of repetition of watermark. [Watermarked Image iscreated]
VI. EXTRACTION OF WATERMARK USING LEAST SIGNIFICANT BIT SUBSTITUTION
Extracting watermark is the process of getting the embedded message from the cover image. The main algorithm for the embedded stage is as follow:
Algorithm:
Step 1 Read watermarked image using imread() function [Returns three 2d array containing the image data]
Step 2 Calculate sizes of watermarked object.
[Mwmk = Height of Image, Nwmk =Width of Image]
Step 3 Extract least significant bit of watermarked object using bitget() function for all the three arrays R,G and B to recreate wateermark
Step 4 Multiply value of each element by 256.

EXPERIMENTAL RESULTS
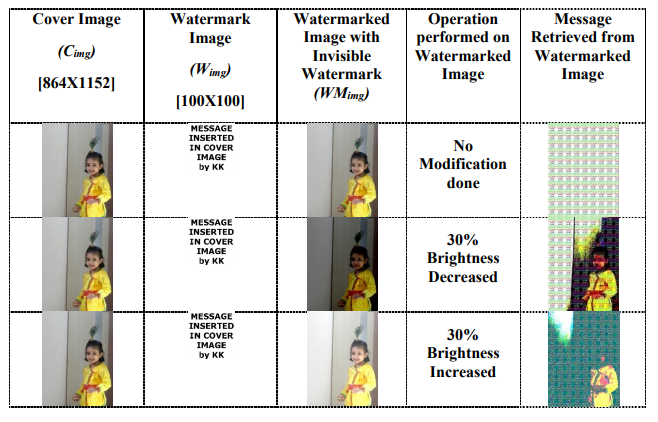
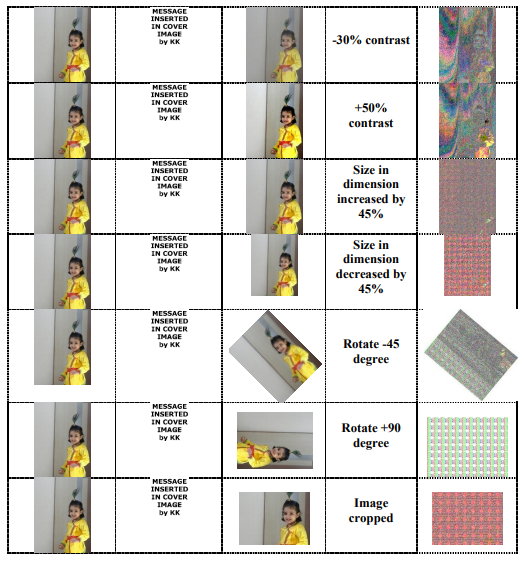
Here in the above table the first column is containing cover image (image which is to watermark, Cimg) than second column contains watermark itself (Wimg). After embedding watermark on cover image we get watermarked image (WMimg) and when we retrieve watermark from WMimg we got it successfully and when we apply some attacks on WMimg like increase and decrease in brightness of image up to 30-
50% WMimg its successfully detected. When we change contrast of image up to 30-50% it’s (WMimg) retrieved at some of the portion and the result is almost same in case of resizing the WMimg. When we crop or rotate the WMimg we are getting some of portion of Wimg and that is sufficient for authenticity.
VII. CONCLUSION
Looking forward to security of images over web, various techniques are used to put check over it and one of them is watermarking. And this paper portrays simple and effective method of LSB security of images implemented in MATLab .The complexity is reduced in the proposed algorithm with reference to computational model. The algorithm is applicable for 8 bit image of the same or different size of cover (RGB) and watermark image (RGB). A good balance between the security and the image quality is almost achieved. The future work will focus on improving the efficiency of the proposed technique.
VIII. SUGGESTED READINGS
BOHRA, K. K. BABY SONAM. JODHPUR.
Fu-an, Z. (2015). A Robust Watermarking Scheme Based on Least Significant Bit and Discrete Cosine Transform*. International Journal of Security and Its Applications , 175-184.
Naini, P. M. (2011). Digital Watermarking Using MATLAB.www.intechopen.com .
Neha Jadhav, S. K. (2015). Digital Watermarking Using Least Significant Bit Algorithm. International Journal of Emerging Technologies and Engineering (IJETE) , 43-46.
Vinay Sahu, K. L. (2013). A New Technique for enhance Image Protection Using Digital Watermarking. International Journal of Innovative Technology and Exploring Engineering (IJITEE) , 171-173.
Zargar, A. J. (2014). Digital Image Watermarking using LSB Technique. International Journal of Scientific & Engineering Research , 202-204.
