pp.27-33
Pooja Soni1 ,Surabhi Agrawal2, Navnit Singh3
Department of Computer Science & Engineering, CGI, Bharatpur1
Department of Computer Science & Engineering, Jagannath University, Jaipur 2
Department of Computer Science & Engineering, AIET, Jaipur3
Abstract: Password theft and stealing has been one of the major issues for the security of any website, which is mostly been in practice due to use of weak text passwords. For convenience people often reuse these passwords for all websites which results in domino Effect. Firstly, in case attacker successes to trace the password, he can misuse it to gain access to more websites. Secondly, there are various password stealing methods such as phishing, malwares which can prone to password theft conveniently with a little knowledge of programming and software. Various other methods such graphical passwords, password management tools and three way authentication techniques were also used to overcome the problem of password attack. In this paper, we introduce a User authentication protocol named OTPAD which requires a user’s cell phone and short message service to prevent password stealing and password reuse attacks. OTPAD only requires each participant to have a unique phone number, and involves a telecommunication service provider in registration and recovery phases. OTPAD uses one time password strategy which is been generated by secure one way hash function along with the triple DES method to make the channel secure in case the password leaks due to single way encryption. After analysing the OTPAD protocol, we find that OTPAD is efficient and affordable compared with the conventional web authentication mechanisms and it is more secure than other authentication techniques also.
Keywords: Network security, User authentication, Hash Function, Triple DES, One-Time Password, OTPAD
INTRODUCTION
User Authentication has been one of the most important component for the website Security. Earlier, Text passwords that were written down manually along with username were considered as the prior mean of user authentication for websites. If user chooses to enter the strong password, it can prevent domino attack, brute force attack and dictionary attacks. Human tendency forces them to use small text strings as their password for easy memorization. Along with this users usually keep the same passwords for most of login websites. Thus as the no. of websites increases, the domain of the password decreases. This efficiently allows the attacker to theft the password and gain access to the significant information.
Till today, researchers have investigated many methods to resolve the issue of password stealing but each of them suffered a considerable drawback. Humans prefers to be more comfortable with remembrance of graphics and thus graphical password scheme[5]-[9] was adopted but it was not mature enough to be widely implemented in practice and still exposed to several attacks. Another approach, Password management Tool is used [10]-[12] which generates the strong password for each website and also helps for password reuse and recall problems. But due to the lack of security knowledge, general users doubt its security and thus feel uncomfortable about using it. It is also important to consider the effects of password stealing attacks. Adversaries steal or compromise passwords and take off users’ identities to launch malicious attacks, collect
sensitive information, perform unauthorized payment actions, or leak financial secrets[13]-[16]. Phishing[17] is the most common and efficient password stealing attack[18]-[20].
To provide more reliable user authentication some researchers worked upon Three-factor authentication rather than password-based authentication. Three-factor authentication depends on three factors i.e. password (what you know), token (what you have), and biometric (who you are). To pass the authentication, the user must input a password and provide a pass code generated by the token (e.g., RSA Secured [21]), and scan her biometric features (e.g., fingerprint or pupil). Three-factor authentication is a complete resistive tool against password stealing attacks, but it involves comparative high cost[22]. Thus, three-factor authentication is overpowered by two-factor authentication is more attractive and practical in use. Although many banks support two-factor authentication, it still suffers from the negative influence of human factors, such as the password reuse attack. Users have to memorize another four-digit PIN code to work together with the token.
In this paper, we introduce a User authentication protocol named OTPAD which requires a user’s cell phone and short message service to prevent password stealing and password reuse attacks. OTPAD only requires each participant to have a unique phone number, and involves a telecommunication service provider in registration and recovery phases. OTPAD, uses one time password strategy which is been generated by secure one way hash function along with the triple DES method to make the channel secure in case the password leaks due to single way
encryption. After analyzing the OTPAD protocol, we find that OTPAD is efficient and affordable compared with the conventional web authentication mechanisms. Therefore, the main concept of OTPAD is to let users free from having to remember or type any passwords into conventional computers for authentication. Unlike generic user authentication, OTPAD involves a new component, the cell phone which comprises an android application, which is used to generate one-time passwords and a new communication channel, SMS, which is used to transmit authentication messages.
- PROBLEM DEFINITION
Due to the large increase in the number of users of Internet in order to perform conventional activities in a convenient way has put a large question over its integrity. Web services facilities such as online banking e-commerce, social networks, and cloud computing has gathered a major section of the world together over a network. But user authentication is mainly held by text passwords for most websites.
Using text passwords has various severe disadvantages. First, since users design their passwords by their own so for easy memorization, users tend to choose relatively short text string passwords for all websites [2]. This behavior causes a risk of a domino effect due to password reuse [1]. Second, humans have tendency to generate a password that resembles close to their personal life and thus a person can judge the passwords many times in such cases such as phone no or birthdate[4]. Florencio and Herley [3] indicated that users forget
Passwords a lot: 1.5% of Yahoo users forget their passwords every month. Some studies pay attention to password management[12], [28]. These approaches could mitigate this problem, but they also make the system more complicated to use. In addition, phishing attacks and malware are threats against password protection.
Therefore, we proposed a user authentication, called OTPAD,to prevent the above attacks. The goal of OTPAD is to prevent users from typing their passwords into conventional systems.
By accepting one-time passwords and doubly encrypting them, password information is no longer important. A one- time password is expired when the current session of the user completes. Rather than using simple Internet channels, OTPAD uses SMS and user’s cell phones comprising android application to avoid password stealing attacks.
- METHODOLOGY
- Architecture of OTPAD and Its Assumption
OTPAD adopts the one-time password strategy [23]; therefore, which is based on method one time password, SMS channel and explain why SMS can be trusted. Finally,
We introduce the security of 3G connection used in the registration and recovery phases of OTPAD.
- One –Time Password
The one-time passwords in OTPAD are generated by a secure one-way hash function. This function will later be encrypted with the triple DES method in order to provide the security in case of failure in exchanging the symmetry key at any point of encryption.
At the early stage with a given input , the set of onetime passwords is established by a hash chain through multiple hashing. Assuming we wish to prepare one-time passwords, the first of these passwords is produced by performing hashes on input c
δi→ HN(c) (1)
The next one-time password is obtained by performing N-1 hashes
δi→ HN-1(c) (2)
Hence, the general formula is given as follows:
δi→ HN-i(c) (3)
In practice, H is realized by SHA-256[24] in OTPAD.
For more security reasons, we use these one-time passwords in reverse order, i.e., using , then . If an old one- time password is leaked, the attacker is unable to derive the next one. In other words, she cannot impersonate a legal user without the secret shared credential .
After this the Password so generated each time would face a double time encryption with triple DES by applying two keys Ksd2 and Ksd3. Triple DES with three keys is highly secure but has a drawback of requiring 56×3=168 bits for the key, which can be slightly difficult to have in practical situations.
There the Password P so generated in each time would go through following three phases:
- Encrypt with key Ksd2. Thus we have Eksd2 (P).
- The output so produced would further be Decrypted with key Ksd3 and thus function would be as such Dksd3 (Eksd2 (P)).
- Further key Ksd2 will be used for encryption of step 2 output as: Eksd2 (Dksd3 (Eksd2 (P))).
SMS Channel
Telecommunication systems provide a text-based communication service known as SMS.OTPAD requires SMS channel against password stealing attacks to construct a secure user. Authentication protocol. Since, SMS is a fundamental service of telecom, which belongs to 3GPP standards [25]. SMS is the most widespread mobile service in the world that represents the most reliable data transmission of telecom systems [26]. In comparison to
TCP/IP network, the SMS network is a secure platform; hence, it raises the effort of internal attacks, e.g., tampering and manipulating attacks. Therefore, SMS is an out-of-band channel that protects the exchange of messages between users and servers. Unlike conventional authentication protocols, users securely transfer delicate messages to servers without trusting on untrusted stands. OTPAD resists password thieving attacks since it is based on SMS channels.
3G Connection
3G connection delivers data confidentiality of user data and signal data to avoid eavesdropping attacks. It also provides data integrity of signal data to avoid altering attacks. The confidentiality and integrity algorithms are f8 and f9, respectively [27].where f8 is a synchronous binary stream cipher and f9 is a MAC algorithm. OTPAD exploits the security features of 3G connection to improve the appropriate account registration and recovery actions. Users can securely transmit and receive information to the website via 3G connection.
IMPLIMENTATION
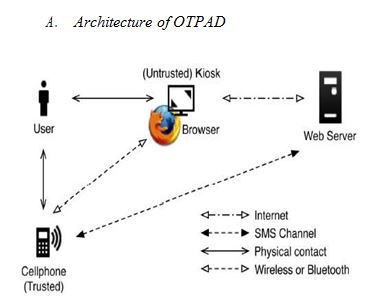
Fig. 1. Architecture of OTPAD system
Fig. 1 describes the architecture of OTPAD to perform the secure login. User must have a cellphone on which an android application is deployed. By launching the application in the cell phone registration should be done. The registration requires to enter the complete details of the user along with a long term one time password.
The user will operate its cellphone and the untrusted system to make secure login to the web server that it wishes to access. The connection between the phone and webserver will be done by establishing SMS channel. The web browser interact with webserver via 3G connection preferably Wi-Fi.
The assumptions in OTPAD system are as follows.
- Each web server possesses a unique phone number. Via the phone number, users can interact with each website through a wifi
- The users’ cellphones are malware-free. Hence, users can safely input the long-term passwords into
- The telecommunication service provider (TSP) will participate in the registration and recovery phases. The TSP is a bridge between subscribers and web servers. It provides a service for subscribers to perform the registration and recovery progress with each web
- Subscribers (i.e., users) connect to the TSP via any internet connections to protect the
- The TSP and the web server establish a secure sockets layer (SSL) tunnel. Via SSL protocol, the TSP can verify the server by its certificate to prevent phishing attacks. With the aid of TSP, the server can receive the correct sent from the
- If a user loses his/her cellphone, she can notify her TSP to disable her lost SIM card and apply a new card with the same phone Therefore, the user can perform the recovery phase using a new cellphone
- Phases of OTPAD
OTPAD consists of registration, login, and recovery phases. We introduce the details of these three phases respectively. Fig. 2 Operation flows for user in each phase of OTPAD system respectively. Black rectangles indicate extra steps contrasted with the generic authentication system :(a) registration, (b) login, and (c) recovery.
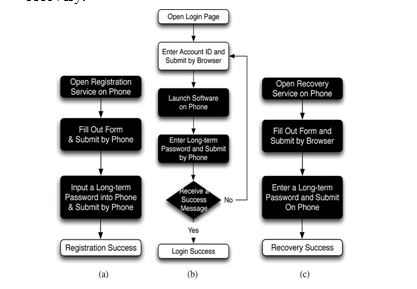
Fig. 2. Phases of OTPAD
The above fig.2 describes the operation flows of users during each phase of OTPAD. Unlike generic web logins, OTPAD utilizes a user’s cellphone as an authentication token and SMS as a secure channel. Different from regular login processes, additional steps are required for OTPAD and are marked in back rectangles in Fig. 2. In the registration phase, a user starts the OTPAD program to register her new account on the website he/she wishes to visit in the future. Unlike conventional registration, the
server requests for the user’s account id and phone number, instead of password. After filling out the registration form, the program asks the user to setup a long-term password. This long-term password is used to generate a chain of one- time passwords for further logins on the target server. Then, the program automatically sends a registration SMS packet to the server for completing the registration procedure. The context of the registration SMS is encrypted to provide data confidentiality by HMAC and triple DES algorithms.
OTPAD also designed a recovery phase to fix problems in some conditions, such as losing one’s cellphone. Contrasting with general cases, login procedure in OTPAD does not require users to type passwords into an untrusted web browser. The user name is the only information input to the browser. Next, the user opens the OTPAD program on her phone and enters the long-term password; the program will generate a one-time password and send a login SMS securely to the server. The login SMS is encrypted by the one-time password with HMAC and triple DES. Finally, the cellphone receives a response message from the server and shows a success message on her screen if the server is able to verify her identity. The message is used to ensure that the website is a legal website, and not a phishing one. Protocol details of each phase are provided as follows.
- Registration Phase
Fig.3. depicts the registration phase. The aim of this phase is to allow a user and a server to negotiate a shared secret to authenticate succeeding logins for this user. The user begins by opening the OTPAD program installed on her cellphone. She enters IDu (account id she prefers) and IDs (usually the website URL or domain name) to the program. The mobile programs end IDu and IDs to the telecommunication service provider (TSP) through a Internet connection to make a request of registration. Once the TSP received the IDu and the IDs, it can trace the user’s phone number Tu based on user’s SIM card. The TSP also plays the role of third-party to distribute three shared keys Ksd1, Ksd2 and Ksd3 between the user and the server. The shared keys Ksd1, Ksd2 and Ksd3 are used to encrypt the registration SMS with HMAC and triple DES algorithm. The TSP and the server will establish an SSL tunnel to protect the communication. Then the TSP forwards IDu, Tu, and Ksd1, Ksd2, Ksd3 to the assigned server S. Server S will generate the corresponding information for this account and reply a response, including server’s identity IDs, a random seed Ø, and server’s phone number Ts. The TSP then forwards IDs, Ts, Ø, and Ksd1 , Ksd2 , Ksd3 shared keys to the user’s cellphone. Once reception of the response is finished, the user continues to setup a long-term password Pu with her cellphone. The cellphone computes a secret credential C by the following operation:
C=H (Pu||IDs||Ø) (4)
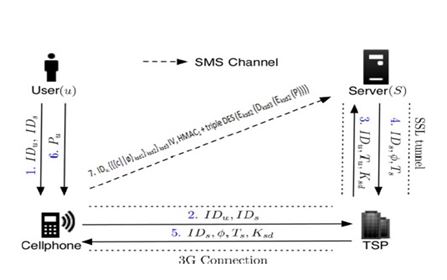
Fig 3. Procedure of Registration Phases
Where Ksd (shared keys) = Ksd1 + Ksd2 + Ksd3 (5)
To prepare a secure registration SMS, the cellphone encrypts the computed credential C with the keys Ksd1, Ksd2 and Ksd3 by HMAC & triple DES algorithms and generates the corresponding MAC i.e., HMAC1 and triple DES (Eksd2 (Dksd3(Eksd2(P)))). HMAC-SHA1 takes input user’s identity, cipher text and IV to output the MAC [29], [30].Then, the cell phone sends an encrypted registration SMS to the server by phone number Ts as follows:
Cell phone → S: IDu; {{{c||ø}ksd1}ksd2}ksd3 IV, HMAC1 + triple DES (Eksd2 (Dksd3 (Eksd2 (P)))) (6)
Server S can decrypt and verify the authenticity of the registration SMS and then obtain C with the shared key Ksd
.Server S also compares the source of received SMS with Tu to pre-vent SMS spoofing attacks. At the end of registration, the cell-phone stores all information {IDs, Ts, Ø, i} except for the long-term password Pu and the secret C. Variable i indicates the current index of the one-time password and is initially set to 0. With i, the server can authenticate the user device during each login. After receiving the message (6), the server stores {IDu, Tu, Ø, c, i} and then completes the registration.
- Login Phase
The login phase begins when the user u sends a request to the server S through an untrusted browser (on a kiosk). The user uses her cellphone to produce a one-time password, e.g., δi, and deliver necessary information encrypted with δi to server S via an SMS message. Based on pre-shared secret credential c, server S can verify and authenticate user u based on δi. Fig. 4 shows the detail flows of the login phase
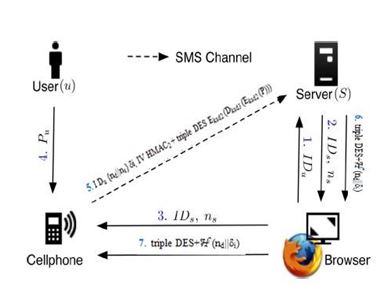
Fig 4. Procedure of Login phase
The protocol starts when user u wishes to log into her favorite web server S (already registered). However, we begin the login procedure by accessing the desired website via a browser on an untrusted kiosk. The browser sends a request to S with u’s account IDu. Next, server S supplies the IDs and fresh nonce ns to the browser. Meanwhile, this message is forwarded to the cellphone through Bluetooth or wireless interfaces. After reception of the message, the cellphone analysis related information from its database via IDs, which includes server’s phone number Ts and other parameters {ø, i}. The next step is advertising a dialog for her long-term password Pu. Secret shared credential C can regenerate by inputting the correct Pu on the cellphone. The one-time password δi for current login is recomputed using the following operations.
C=H (Pu||IDs||Ø) (7)
δi→ HN-i (c) (8)
The cellphone generates a fresh nonce nd. To prepare a secure login SMS, the cellphone encrypts nd and ns with δi and generates the corresponding MAC, i.e., HMAC2 and triple DES (Eksd2 (Dksd3 (Eksd2 (P)))). The next section on the cellphone is sending the following SMS message to server S:
Cellphone→ S: I Du {nd||ns} δi, IV HMAC2 + triple DES (Eksd2 (Dksd3 (Eksd2 (P)))) (9)
After receiving the login SMS, the server recomputed δi (i.e., δi=HN-i(c)) to decrypt and verify the authenticity of the login SMS. If the received ns equal the previously generated ns, the user is authentic; otherwise, the server will reject this login request. Upon successful verification, the server sends
back a success message through the Internet triple DES + H(nd||δi) to the user device. The cellphone will verify the received message to ensure the completion of the login procedure. The last verification on the cellphone is used to prevent the phishing attacks and the man-in-the-middle attacks. If the verification is failed,the user knows the failure of login, and the device would not increase the index i. If the user is successfully log into the server, index i is able to automatically increased i=i+1 in both the device and the server for synchronization of one-time password. After N-1 rounds, the user and the server can reset their random seed ø by the recovery phase to refresh the one-time password.
- Recovery Phase
Recovery phase is designated for some specific conditions for an example; a user u may lose her/his cell phone. The protocol is able to recover OTPAD setting on her new cellphone assuming she still uses the same phone number (apply a new SIM card with old phone number).
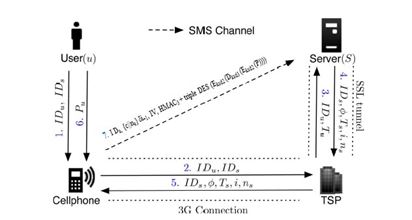
Fig.5. Procedure of Recovery Phase
Fig.5.shows the detail flows of recovery phase. Once user u installs the OTPAD program on her new cellphone, she can launch the program to send a recovery request with her account IDu and requested server IDs to predefined TSP through a 3G connection. As we mentioned before, IDs can be the domain name or URL link of server S. Similar to registration, TSP can trace her phone number Tu based on her SIM card and forward her account IDu and the Tu to server S through an SSL tunnel. Once server S receives the request, S examines the account information in its database to confirm if account u is registered or not. If account IDu exists, the information used to calculate the secret credential C will be fetched and be sent back to the user. The server S generates a fresh nonce ns and replies a message which consists of IDs, ø, Ts, i, and ns. This message includes all necessary elements for generating the next one-time passwords to the user u.
When the mobile program receives the message, like registration, it forces the user u to enter her long-term password to reproduce the correct one-time password δi+1 (assuming the last successful login before lost her cellphone is δi). During the last step, the user’s cellphone encrypts the secret credential C and server nonce ns to a cipher text. The
recovery SMS message is delivered back to the server S for checking. Similarly, the server S calculates δi+1 and decrypts this message to ensure that user u is already recovered. At this point, her new cellphone is recovered and ready to perform further logins. For the next login, one-time password δi+2 will be used for user authentication.
RESULTS AND ANALYSIS
User implemented a prototype of OTPAD according to its three phases. The prototype consists of three components: a mobile program running on Android smart phones (Android OS v2.1); an extension on Firefox browser; and a web server. The server offers a web service by an Apache server running on a work station with Windows and SMS service with a GSM modem connected to itself. The communication interface between the phone and the browser extension is based on a client/server model over the TCP/IP network. Phones use their Wi-Fi or 3G to connect the TCP server is built by the extension. Other mediums, such as Bluetooth and cable line, can substitute for current communication interface. Moreover, we reduced the amount of user interactions and optimize the whole performance in all components.
We developed the client program on Android OS due to its popularity and generality. The program has been established and conducted on any android mobile phone. For safety operations, fundamental information of OTPAD is kept safe in an encrypted SQLite database with as an encryption key. After installing the program, a user creates an account to a website via the registration procedure. Upon successful registration, the user can log into the website. To make the progress smooth, the user only has to key in her long-term password and select a website. Then the remaining operations would perform program through clicking a button. All required interactions are eliminated to ensure OTPAD’s efficiency.s
In the web server implementation, we developed a server program which consists of main server codes (JAVA) and setup scripts for database (MYSQL). Server program can be installed and performed on a Glass Fish server HTTP server.
Comparisons between OTPAD and Other Systems
The account setup process is classified into two types: physical and logical setup. MP-Auth, Phoolproof, and Wu et al.schemes all assume that users must setup their accounts physically. They establish shared secrets with the server via a secret (conceals) out-of-band channel. For example, banks often require users to setup accounts personally through physical contact or utilize the postal service. Conversely, OTPAD deployed an alternative approach, logical account setup, which allows users to build their accounts without physical contact with the server .In the OTPAD system, we assume a TSP in the registration phase to accomplish as the same security as physical account setup. OTPAD inherits existing trust relations between the TSP and the subscribers
(i.e., users) in the telecommunication system. The users’ identities were authenticated by the TSP when they applied their cellphone numbers. With this trust relation, users can smoothly setup their accounts via cellphones without physical contact. OTPAD provides the more security then other system by using triple DES algorithm with hash function.
Table 1. Comparison between different authentication protocols
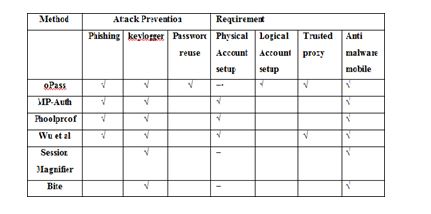
Table 1. Summarizes comparisons of OTPAD with previous systems. Symbol ‘√’ indicates that the system prevents against the attack, ‘•’ represents the special requirement is needed, and ‘‾’ means not applicable.
CONCLUSION
In this paper, we proposed a user authentication protocol named OTPAD which leverages cellphones and SMS to thwart password stealing and password reuse attacks. We assume that each website possesses a unique phone number. We also assume that a telecommunication service provider participates in the registration and recovery phases.
A prototype of OTPAD is also implemented to measure its performance. The average time spent on registration and login is 21.8 and 21.6 s, respectively. According to the result, SMS delay occupies more than 40% of total execution time. The delay could be shorter by using advanced devices. Besides, the performance of login of OTPAD is better than graphical password schemes, for example, Pass faces. The login time of Pass faces is from 14 to 88 s, which is longer than OTPAD [31]. Therefore, we believe OTPAD is acceptable and reliable for users.
- REFERENCES
[1]Hung-Min Sun, Yao-Hsin Chen, and Yue-Hsun Lin,“The domino effect of password reuse,”IEEE Transactions On Information Forensics And Security, Vol. 7, No. 2, April 2012
Ives, K. R. Walsh, and H. Schneider, “The domino effect of password reuse,” Commun. ACM, vol. 47, no. 4, pp. 75–78, 2004.
- Gawand E. W. Felten, “Password management strategies for online accounts,” in SOUPS ’06: Proc. 2nd Symp. Usable Privacy. Security, New York, 2006, pp. 44–55, ACM.
- Florencio and C. Herley, “A large-scale study of web password habits,” in WWW ’07: Proc. 16th Int. Conf. World Wide Web. New York, 2007, pp. 657–666, ACM.
- Chiasson, A. Forget, E. Stobert, P. C. van Oorschot, and R. Biddle, “Multiple password interference in text passwords and click-based graphical passwords,” in CCS ’09: Proc. 16th ACM Conf. Computer Communications Security, New York, 2009, pp. 500–511, ACM.
- Jermyn, A. Mayer, F. Monrose, M. K. Reiter, and A. D. Rubin, “The design and analysis of graphical passwords,” in SSYM’99: Proc. 8thConf. USENIX Security Symp., Berkeley, CA, 1999, pp. 1–1, USENIX Association.
- Perrig and D. Song, “Hash visualization: A new technique to improve real-world security,” in Proc. Int.Workshop Cryptographic Techniques E-Commerce, Citeseer, 1999, pp. 131–138.
- Thorpe and P. van Oorschot, “Towards secure design choices for implementing graphical passwords,” presented at the 20th. Annu. Computer Security Applicat. Conf., 2004.
- Wiedenbeck, J. Waters, J.-C. Birget, A. Brodskiy, and N. Memon, “Passpoints: Design and longitudinal evaluation of a graphical password system,” Int. J. Human-Computer Studies, vol. 63, no. 1–2, pp. 102–127, 2005.
- Wiedenbeck, J. Waters, L. Sobrado, and J.-C. Birget, “Design and evaluation of a shoulder-surfing resistant graphical password scheme,” in AVI ’06: Proc. Working Conf. Advanced Visual Interfaces, New York, 2006, pp. 177–184, ACM.
- Pinkas and T. Sander, “Securing passwords against dictionary attacks,” in CCS ’02: Proc. 9th ACM Conf. Computer Communications Security, New York, 2002, pp. 161–170, ACM.
- A. Halderman, B. Waters, and E. W. Felten, “A convenient method for securely managing passwords,” in WWW ’05: Proc. 14th Int. Conf. World Wide Web, New York, 2005, pp. 471–479, ACM.
- -P. Yee and K. Sitaker, “Passpet: Convenient password management and phishing protection,” in SOUPS ’06: Proc. 2nd Symp. Usable Privacy Security, New York, 2006, pp. 32–43, ACM.
- Dhamija, J. D. Tygar, andM. Hearst, “Why phishing works,” in CHI ’06: Proc. SIGCHI Conf. Human Factors Computing Systems, New York, 2006, pp. 581–590, ACM.
- Karlof,U. Shankar, J. D.Tygar, andD.Wagner, “Dynamic pharming attacks and locked same-origin policies for web browsers,” in CCS ’07: Proc. 14th ACMConf. Computer Communications Security, New York, 2007, pp. 58–71, ACM.
- Holz, M. Engelberth, and F. Freiling, “Learning more about the underground economy: case-study of key loggers and drop zones,” Proc. Computer Security ESORICS 2009, pp. 1–18, 2010.
- Provos, D. Mcnamee, P. Mavrommatis, K. Wang, and N. Modadugu, “The ghost in the browser: Analysis of web-based malware,” in Proc. 1st Conf. Workshop Hot Topics in Understanding Botnets, Berkeley, CA, 2007.
- Phishing Activity Trends Rep., 2nd Quarter/2010 Anti-Phishing Working Group [Online]. Available: http://www.antiphishing.org/
- Parno, C. Kuo, and A. Perrig, “Phoolproof phishing prevention,” Financial Cryptography Data Security, pp. 1–19, 2006.
- Yin, D. Song, M. Egele, C. Kruegel, and E. Kirda, “Panorama: Capturing system-wide information flow for malware detection and analysis,” in CCS ’07: Proc.e 14th ACM Conf. Computer Communications Security, New York, 2007, pp. 116–127, ACM.
- Garriss, R. Cáceres, S. Berger, R. Sailer, L. van Doorn, and X. Zhang, “Trustworthy and personalized computing on public kiosks,” in Proc. 6th Int. Conf. Mobile Systems, Applications Services, 2008, pp. 199– 210, ACM.
- RSA SecureID [Online]. Available: http://www.rsa.com/node.Aspx?id=1156/
- O’Gorman, “Comparing passwords, tokens, and biometrics for user authentication,” Proc. IEEE, vol. 91, no. 12, pp. 2021–2040, Dec. 2003.
- Lamport, “Password authentication with insecure communication,” Commun. ACM, vol. 24, pp. 770–772, Nov. 1981.
- Gilbert and H. Handschuh, “Security analysis of SHA-256 and sisters,” in Selected Areas Cryptography, 2003, pp. 175–193, Springer.
- TS 23.040: Technical Realization Short Message Service (SMS) 3GPP [Online]. Available: http://www.3gpp.org/
- T. Report, ITU Internet Rep. 2006: Digital. Life [Online].Available: http://www.itu.int/
- TS 35.201: Specification 3GPP Confidentiality Integrity Algorithms Document 1: f8 and f9 Specification 3GPP [Online]. Available: http:// 3gpp.org/
- Ross, C. Jackson, N. Miyake, D. Boneh, and J. C. Mitchell, “Stronger password authentication using browser extensions,” in SSYM’05: Proc. 14th Conf. USENIX Security Symp., Berkeley, CA, 2005, pp. 2–2, USENIX Association.
- Bellare and C. Namprempre, “Authenticated encryption: Relations among notions and analysis of the generic composition paradigm,” Advances Cryptology—ASIACRYPT 2000, pp. 531–545, 2000.
- Krawczyk, “The order of encryption and authentication for protecting communications (or: How secure is SSL?),” in Advances Cryptology— CRYPTO 2001, 2001, pp. 310–331.
- Biddle, S. Chiasson, and P. van Oorschot, “Graphical passwords: Learning from the first twelve years,” in ACM Computing Surveys, Carleton Univ., 2010.
