- INTRODUCTION
Health surveillance can be conducted in both home environments and both: [11] Low cost and delivery of citizen-centered care solutions for predetermined challenges. [9] Recent advances in sensor communication, sensor sensing and microelectronics are aimed at monitoring and managing chronic diseases and detecting potential emergencies. [10] Health surveillance in domestic settings can be carried out in two ways or both [11]: minor electronic components are responsible for the monitoring and administration of chronic diseases and the determination of medical conditions. emergency. [10] Health surveillance can be carried out both in domestic environments and both [11]. Low cost and delivery of citizen-centered care solutions for predetermined challenges. [9] Recent advances in sensor communication, sensor sensing and microelectronics are aimed at monitoring and managing chronic diseases and detecting potential emergencies. [10] Two observations of health observation at home or both can be managed: [11]: home health monitoring can be managed by one or both: [11] the cost of major challenges and citizen-centered care. solutions [9] Recent advances in sensor communication, sensor sensing and microelectronics include monitoring and managing chronic diseases and detecting potential emergencies [10].
Two health observations can be managed in the home or both: [11]: Home health monitoring can be managed by any of the following systems: [11] The cost of the main challenges and citizen-centered care solutions [9]. Recent advances in sensor-based communication, sensing and microelectronics include monitoring and managing chronic diseases and detecting potential emergencies. [10] Health surveillance in domestic settings can be carried out in two ways or both [11]: minor electronic components are responsible for the monitoring and administration of chronic diseases and the determination of medical conditions. emergency. [10] Health surveillance in domestic environments can be carried out in one or both ways [11]: minor electronic components are responsible for the monitoring and administration of chronic diseases and the determination of medical conditions. urgency [10].
1.1 Use of smart watch for health monitoring
In addition, mobile devices improve access to patient information support, as well as the care of the person with dementia (at home). Formal carers can be an alternative to their work. Different sensor technologies are currently being used to monitor emergency situations (eg, collapse detection, roaming), but a consistent, non-intrusive, comfortable and reliable process is required to monitor physical health over time. daily activity.

Fig. 1: Health Care Analysis over IoT Device
2. Review of Literature
[SharadaSaxen et al., 2013] Security method for cloud migration data. Cloud computing combines different computing and Internet concepts and creates an idea that provides a platform for flexible and cost-effective business applications. Migration of data in the current situation, Security Cloud users move your data and applications to the heart of the user’s concerns. Many companies and organizations are continuing their efforts to reduce IT costs, and as a result, [20] IT organizations and virtualization technologies are contributing to their use. Cloud computing provides a good infrastructure and a good cost for the organization with reduced administration. The type of application or cloud platform is defined.
Cloud computing is different from the paradigmatic and evolving cloud, which is why customers are asking on demand and especially how to claim it. Cloud computing, security issues for many businesses, sharing of resources with other unchecked agencies, cloud storage service discrepancies, key cryptography, data integrity and legitimate government laws, licenses and data on cloud computing state of Internet security.
[Alkhalil Adel. 2016]Recommended decision model – cloud migration. The development of cloud services is advantageous for IT architectures and organizations, new services and the quality of IT companies. Increase the capacity of cloud service systems and system services. And it offers better quality of service, high performance and service costs. Provides the flexibility to meet the cloud-based needs of KBDSS (decision support knowledge) and cloud solution resources. Therefore, to develop a model for a cloud-based copyright migration system, it takes three. The first method is the subject that motivates and affects the data migration. Identify user needs for the development of the main business problem models. [22] Secondly, there are several departments within the organization, IT, security and cloud providers, and many others. According to the author, more cloud than expected with the local data center. The third part is a decision-making model composed of three elements of intelligence and design.
[Nur Ibrahim Hussein el.al 2013] Proposed Requirements for Migration of Existing Systems and Cloud Security. Cloud computing is an appropriate technology and a useful technology. There are benefits for many companies and organizations. Migrating a cloud server to the cloud server is very difficult to manage more than migrating to other cloud servers. During migration, it does not show data location and data location, but succeeds at the cloud server by selecting migration, scheduling, and data transfer from the server. Data migration requirements require information security during migration. Security issues are also problematic for businesses, organizations and users. In this document, the time and subsequent security requirements for migrating data from the cloud server of the operating system. And when cloud server data migration is another cloud. [23]
[Dinash Goal et al. 2014] Using this process, improving the security of data migrations provides random key encryption levels. Data protection has become an important issue for data protection. Indeed, applications and data servers have been removed. They can no longer rely on the external auditor (TPA) of the confidentiality or confidentiality of the user or agency. Data migration is a method of transmitting information from a computer system to a cloud or other server. [24] Provides efficient data transfers, loading and retrieval of data to information from one system to another. Design details include system details and system format, system requirements, specifications, and other necessary details.
Yukin and Zuck, 2017 [8]A category with a well-known class processes intermediate or intermediate quality training data provided by the proposed support vector machine (SVM OCC). Their main idea is to represent each of the information provided by the specific set of weight specifications. Depending on the value of the value of their interval of the amount of representation, the amount of valuable data value based on the amount of valuable data is based on an uncertain weight or weight sets. It can also be noted that the interval is replaced by attention to the uncertain weight or probability of uncertainty.
SoH and Miller 2015 [12] New groups recommended Based on CBB-based prevention barriers (CBB) in the promotion of learning support (SL) algorithms. CBB shares training data from similar perspectives in clusters of their viewpoints and integrates these groups directly into the recovery process. The CBB attempts to address two specific limitations of the two current incentives, both of which result in an inappropriate focus on the formation of inappropriate training information. The first filter for the following information appears when the learning information contains the problem area and / or the label and the second is required to know the appropriate organization suitable for that purpose.
3. Proposed Method
3.1. Building the Model of Clustering
Cardiologists define a common wave of the ECG pattern. We repeat this scheme with the previous model driven by heart rate and compare this model with these observations and compare it.
A common model of cardiovascular disease pushes the construction activity, we treat an ECG (based on a specific patient or a group of many patients) that divides pieces superimposed about 3.1 seconds, then a size grouping algorithm Similar.
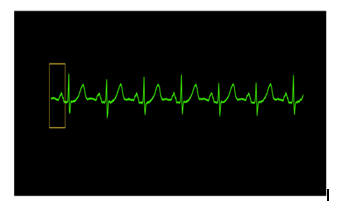
Fig. 2: Heart bit Data Analysis
The clustering algorithm detects a group that takes place during information collection. In the classification, the algorithm analyzes the samples in the input samples and groups the inputs. Cigarette algorithm group observations include clusters associated with clusters with the mean closest to the cluster center.
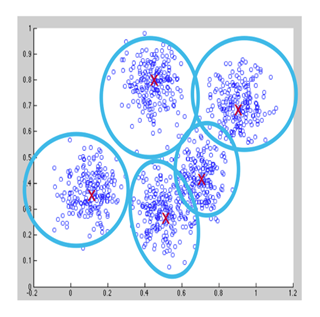
Fig. 3: Cluster of Heart bit Data Analysis
3.2. Apache Spark Code
- AVG data separator breaks.
- Create AK-MEOBJET and set maximum repetition to parameters and clusters to determine the number of clusters.
- Input data model train.
- Save the model for later use.
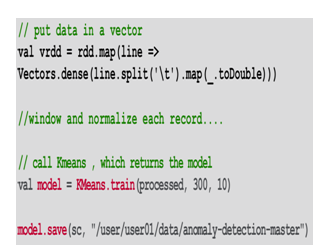
Fig. 4: Sample Code for Machine Learning Model
The result is a catalog of forms that can be used to reconstruct what must look like an EKG.
3.4. Detecting anomalies
Anomalies are the real problem when detecting objects less false alarms; the challenge is how to resize triggers for shape triggers. T-digest is a strategy to determine the extent of the reconstruction error based on the distribution of data sets. The algorithm can be added to an anonymous detection stream so that you can set the number of alarms as a percentage of the total observations. T-digest correctly assumes an allocation with low utilization rates, especially the tail (which is usually the most striking part). And guess, you can use the threshold to create an alert. For example, the determination of the 99% threshold will often be updated for each reconstruction, which will result in a large number of reports (the differences must be rare by definition). 99.9%, an alert can be made for every one thousand reconstructions.
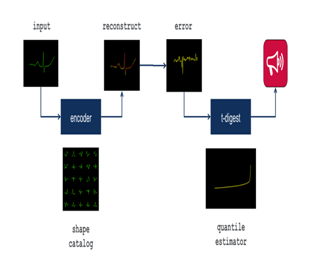
Fig. 5: T-Digest Model
- Observations, Result & Discussion
There are many applications in the data mining telecommunications, analysis of financial data analysis and much more. A growing study of medical informatics is producing huge amounts of information. The analysis of such a large amount of information is very difficult and requires additional knowledge. E Healthcare Diagnostic Health Application Data Mining and Telecommunication. Some patients require a permanent medical examination and need help immediately. E-Health is primarily used to analyze patient data and diagnose different levels. CART Decision Tree Algorithm (Classification and Regression Tree), ID 3 (Repetitive Dicotyamide 3). Select this algorithm to divide, divide a node and divide the stop class of the undivided node.
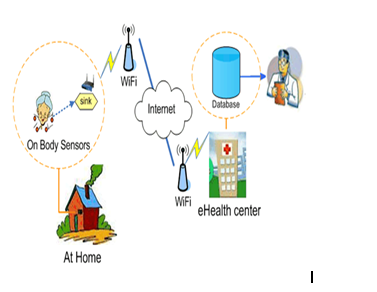
Fig. 5: IoT Based Health Care Model
4.1. Association Rule
The rule mining association is a set of central function binary variables that combine with the transaction database [8], but the feature selection is related to the problem group, which specifically identifies the movements in courses associated with it. The association manages algorithms such as Incapable, CDA, DDA and attraction measures. Smart shirts are designed [10]. The liner can measure electrocardiogram (ECG) and acceleration signals for continuous, real-time medical monitoring of the patient. The sign of the body of the shirt consists mainly of a sensor and a conductive material. The measured body signals are transmitted via a base station and an IEEE 802.15.4 server PC. Portable devices are small enough to cost less in energy and shirt. Words associated with the ECG signal have been proposed to reduce an adaptive filtering method.
In the future, some instruments will contribute to the patient’s physical information (such as heart rate, blood pressure) and other household appliances and appliances around the patient (eg, humidity, temperature, level of carbon monoxide). These physiological and environmental data can identify the patient’s health status and external causes can identify the condition. In some cases, the device group can capture data (for example, carbon monoxide detectors can reach levels above safe limits, open a protocol to open Windows, listen to alarms, and activate functions.
It allows us to analyze our different types of intelligent health forecasting systems. It is true that home care can not be provided to the patient on 24/07/2014. However, a smart watch control device, such as the Basic B1, is formally responsible for providing user health information, at the time, not covered by visiting supervisors. Especially for older patients with cognitive impairment – where self-report methods can be incredible, if not impossible – these devices can provide an estimate of the patient’s daily activities. Of course, the measurement of the device may be different depending on the profile / background of the user and his state of health.
4.2. Using Smart Watches for Health Monitoring
In our case, although the BASIS B1 smartwatch is a new concept of the patient’s daily conceptions, the information collected can not be interpreted as correct and valid medical information, but their texts can trigger specific health care services. Improve patient care and safety. Wellsfair (non-medical) devices such as BASIS B1, in all cases, important aspects of home care such as screening, physical examination, and replacement of patient time. The acquired measures can provide useful information / advice and there is a “free space” in the structure of the usual health care model due to lack of health. Effective e-experimental functionality of smartwatch control devices, in real-world conditions and in real samples, without quantitative methods, without specimens and common features, posing problem.
These problems are used to see the smart watch for health monitoring
If the project is verified by the doctor, it can be used to ensure the health, safety and quality of life of the patient.
4.3. Snapshot of Implementation Models
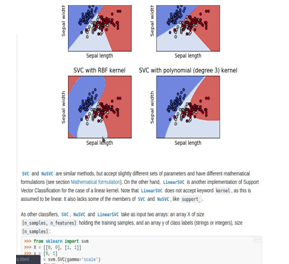
Fig. 6: Different Scatter plot of SVM
Fig. 7: Python script
4.4. Results and Discussion
We have to analyze the data and found the next thing.
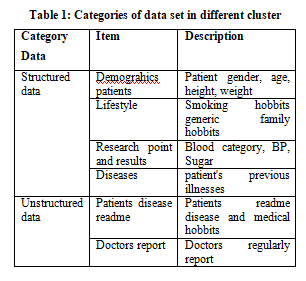
The hospital data used in this study are the data stored in actual hospital data and information centers. To protect privacy and patient protection, we have a secure access mechanism. Information by hospital DSE, information on medical images and gene information We use a three-year data set. Our database of clinical service data includes 31,288,848 patient records out of 31,919 patients. The Clinical Information Department consists primarily of undefined textual information. Structural information includes laboratory information and the age of the patient, such as patient age, sex, and lifestyle. The undefined textual information includes his health account.
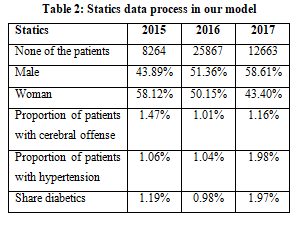
CONCLUSIONS
Data mining is very important in medicine and represents a complete process that requires a comprehensive understanding of health care needs. Health is a major sector that benefits from the establishment and use of information systems. We have an overview of data mining applications in the areas of infrastructure, administration, finance and clinical health services. The knowledge gained through the use of data mining technology can be used to make an effective decision that will improve health care and the success of patient health services. In order to measure the results of data mining, systems may be needed for reporting and monitoring with appropriate analytical technologies and strategies.
REFERENCES
[1] Han, J., Kamber, M:. “Data Mining Concepts and Techniques”, Morgan Kaufmann Publishers, 2006.
[2] K. Mar y Obenshain, MAT “Application of Data Mining Techniques for Healthcare Data “Infection Control and Hospital Epidemiology 2004
[3]Abdullah A. Aljumah , Mohammed GulamAhamad , Mohammad Siddiqui Khubeb“Application of data mining: Diabetes care in young and old patients” in 2012.
[4] Koh HC1, tan G. “Data mining applications in healthcare”, Spring 2005.
[5] Bennett C. Doub T (2011) Data mining and electronic medical records: selecting optimal clinical treatment inpractice. CORR abs / 1112: 1668.
[6] Estella F, Delgado-Marquez BL, Rojas P, Valenzuela O San Roman B. Rojas I (2012) Advanced System automously classify brains MRI in neurodegenerative disease In: International Conference on Multimedia Computing and Systems (ICMCS 2012). IEEE, based in New York, USA, Tangier, Morocco, pp 250-255.
[7] Mahboob Khan “Smart Health Prediction Using Data Mining “, Spring 2015.
[8]Obenshain, MK: “Application of Data Mining Techniques for Healthcare Data” Infection Control and Hospital Epidemiology, 25 (8), 690-695 2004.
[9] Ledbetter C. Morgan, M. “Toward Best Practice: Making use of the Electronic Patient Record as Clinical Data Warehouse”. JOURNAL OF HEALTH information management, VOL 15; PART 2, pages 119-132 2001.
[10] Strisland, F .; Sintef; Svagard, I .; Seeberg, TM (2013) “ESUMS: A mobile system for continuous supervision of the home rehabilitation patient”, in the Proceedings of the 35th IEEE Annual International Conference on Engineering in Medicine and Biology Society, 3-7 July 2013, Osaka, pp. 4670-4673.
[11] Bourouis, A., Feham, M., and Bouchachia, A. (2011), “Ubiquitous Mobile Health Monitoring System for the Elderly (UMHMSE),” International Journal of Computer Science and Information Technology, Vol.2, No. 3, June, pp. 74-82.
[12] Varbol, Peter. “Next-Generation Internet Appliances,” Computer Design, March 1998, pp. 22-24.
[13] Lei Clifton, Clifton A. David, Mark Pimentel AF, Peter J. Watkinson, and Lionel Tarassenko (2014), “Predictive Monitoring of mobile patients by a combination of clinical observations with data from wearable sensors”, IEEE Journal of Biomedical and health informatics, Vol. 18, No. 3, May, pp. 722-730.
[14] Wang Xiaoliang; QiongGui; Bingwei Liu; Zhanpeng Jin et al (2014), “Enabling Smart personalized healthcare: a hybrid cloud approach for Mobile ECG Telemonitoring”, IEEE Journal of Biomedical and Health Informatics, Vol. 18, No. 3 May, page 739 -. 745
[15] Orlando REP, Caldeira, MLP Lei S., and Rodrigues, JPC (2014), “Efficient and Low Cost Windows Mobile BSN Monitoring System Based on TinyOS”, Journal of Telecommunication Systems, Vol. 54, No. 1, pp. 1-9.
[16] Dunsmuir, D., Payne, B .; Cloete, G .; Petersen, C. (2014), “The development of m-Health applications for Pre-eclampsia Triage”, IEEE Journal of Biomedical Informatics and Health, Vol. PP, No. 99 January, p. 2168-2194.
