Cloud Computing Security Issue and Its Proposed Solution
Rajni Kumari , M.Tech Research Scholar ,Center of Cloud Infrastructure and Security,
Suresh Gyan Vihar University , Jaipur , Rajasthan.
E-mail-: rmanushendra@gmail.com
Dr. Manish Sharma , HOD, Center of Cloud Infrastructure and Security, Suresh Gyan
Vihar University , Jaipur , Rajasthan.
E-mail-: manish.sharma@mygyanvihar.com.
Dr. Rashid Hussian, Associate Prof., Electronic and communication, Suresh Gyan
Vihar University, Jaipur, Rajasthan.
E-mail-: rashid.hussian@mygyanvihar.com.
Abstract
Keywords: Cloud Computing, cloud storage and cloud security.
In Recent time, cloud computing drastically change the view of IT infrastructure such as hard-disk, RAM, Software and storage etc. and also perception of everyone. Amazon ,IBM, Google’s Application, Microsoft Azure etc., are the provider of cloud service Provider that provide the developing Applications for client in cloud condition. Furthermore, to get to them from anyplace, any time. Cloud computing includes elements from parallel computing, utility computing, Fog Computing and grid computing and into an innovative deployment architecture in the virtual environment. The main purpose of this paper is identify the issue of cloud data storage and its solution.
1. Introduction
CLOUD COMPUTING: SECURITY ISSUES
1.1 CLOUD SERVICES
There are different service model is offered by cloud: Programming as a Service, Infrastructure as a Service and Platform as a Service separately otherwise called SaaS, IaaS and PaaS. Every one of them have likewise various sorts of sending models, making it imperative to get that system of cloud computing is change. The main security concerns, however, keep on the same
In addition to, with data storage security issues, the moving data over networks is also included by cloud service. The level of network security is required for it and file transfer encryption. The service user and the service provider have responsibility for this. The reliable and trustworthy networks is only chosen by user and use sufficiently secure password and username credentials. The service encryption must be assured by service provider and server-end security for the stored information.
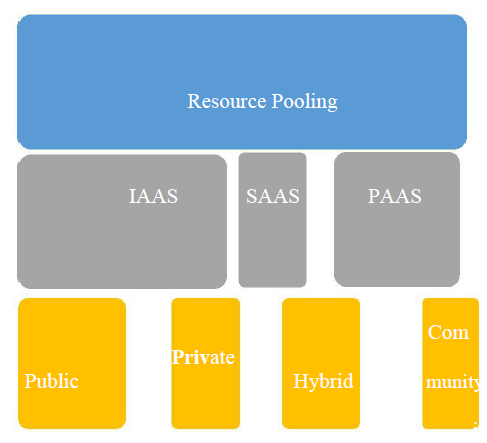
Fig.1 Cloud Computing Model
1.2 KEY SECURITY ISSUES IN CLOUD COMPUTING
Applications, platforms and infrastructure segments are consist in cloud computing. Different products for businesses and individuals around the world have different offer by each segment. Programming as a Service (SaaS), Utility Computing, Web Services, Platform as a Service (PaaS), Service Commerce and Internet Integration are included by business application. Security issues for cloud computing is various are:
Virtual Machine Security
Data Transmission
Access to Servers & Applications
Network Security
Data Integrity
Data Segregation
Patch management
Data Privacy
Data Security
Data Availability
Security Policy and Compliance.
1.3 VIRTUAL MACHINE SECURITY:One of the significant segments of a cloud is Virtualization. It is dynamic for example to past occasions, stopped and restarted could be slipped by, similarly effectively. Guaranteeing that on the equivalent physical machine different instances are running and remote from each other is a major task of virtualization. It can also be readily cloned and easily moved between physical servers. VM collapse makes it difficult to achieve and maintain reliable security by this dynamic nature and potential. Vulnerabilities that are found errors may be unintentionally propagated. Also, to maintain an auditable record is difficult of the security state at any given point of a virtual machine in time. There are two type of virtualization, one of them is full Virtualization and other is Para Virtualization in a cloud computing environment.
Complete hardware architecture of computer is replicated virtually in the full virtualization. However, it is modified so that it can be run parallel in para-virtualization with other operating systems. Abstracts the physical resources is abstracted by VMM (Virtual Machine Monitor) that is a product layer utilized by the various virtual machines. A virtual processor and other virtualized renditions of framework gadgets like I/O gadgets, stockpiling, memory, and so forth are provided by VMM. In all popular VMMs many vulnerability are found that allow avoidance from Virtual machine. It could permit a visitor working framework client to execute code on the host or another visitor working framework by Vulnerability in Microsoft Virtual PC and Microsoft Virtual Server. It is find that vulnerability in VMware’s shared organizers component that awards clients of a visitor framework read and composes access to any piece of the host’s document framework including the framework envelope and other security-touchy records. Weakness in Metasploitable can be broken by clients of a visitor area to execute subjective directions. On host and visitor working frameworks is the other issue is the run of administrator. Current perfect isolation is not offered by VMM. We have taken virtual box of oracle and create A virtual machine of metasploitable and it is easily accessible by root user.
Fig 2: Virtual Box
Fig 3: Virtual Machine
1.4 DATA SECURITY:
The service ofcloud computing that offer for user is easy to find possible storage. Hypertext Transfer Protocol (HTTP) is communication protocol that is used to achieve the service of cloud computing. Data integrity and information security are assured by it, the most common adoption are Hypertext Transfer Protocol
Secure (HTTPS) and Secure Shell (SSH). In a Customaryon proof application organization model, the delicate information of every endeavor keeps on living inside the venture limit and is liable to its physical, legitimate and staff security and access control approaches. Notwithstanding, the undertaking information is put away outside the endeavor limit, at the Service supplier end in distributed computing. In this way, the specialist co-op must embrace extra security checks to guarantee information security and avoid gaps because of security vulnerabilities in the application or through malignant representatives. This includes the utilization of solid encryption procedures for information security and fine-grained approval to control access to information. Cloud specialist organizations, for example, Amazon, the Elastic Compute Cloud (EC2) overseers don’t approach client cases and can’t sign into the Guest OS. EC2 Administrators with a business need are required to utilize their individual cryptographically solid Secure Shell (SSH) keys to access a host. Every single such access are logged and routinely examined. While the information very still in Simple Storage Service (S3) isn’t scrambled of course, clients can encode their information before it is transferred to Amazon S3, so it isn’t gotten to or messed with by any unapproved party.
SOLUTIONS TO DATA SECURITY ISSUE
To secure information it is better solution to encryption. It is smarter to encode information before putting away information in cloud server. Authorization can be given by information proprietor to specific gathering part with the end goal that information can be effectively gotten to. Data access control is provided by data centric security. To improve the data security over cloud is design data security model that include data encryption, data integrity and authentication. Data protection can be used as a service for ensuring privacy. Applying encryption on data to avoid access of data from other users. Before uploading data into the cloud the users are recommended to verify whether the data is stored on backup drives and the keywords in files remain unchanged. The hash of the file is calculated before uploading to cloud servers will ensure that the data is not changed. It can be used for data integrity but it is very difficult to maintain it. To combining identity based cryptography and RSA Signature can be provided to check by RSA based data integrity. Both at the physical level and application level to keep apart data from different users and must be clear boundaries that ensure by SaaS. In cloud computing, Dispersed access control design can be utilized for access management.
Reference
[1]. Data Security Challenges and Its Solutions in Cloud Computing R. Velumadhava Raoa,*, K. Selvamanib,* a Department of Computer Science & Engineering, RIT, Chennai,indiab Department of Computer Science &
Engineering, Anna University, Chennai, India
[2]. Future Generation Computer Systems Addressing cloud computing security issues, Dimitrios Zissis ∗, Dimitrios
Lekkas Department of Product and Systems Design Engineering, University of the Aegean, Syros 84100, Greece
[3]. State-of-the-art Survey on Cloud Computing Security Challenges, Approaches and Solutions Farrukh Shahzada a King Fahd University of Petroleum and Minerals, Dhahran, KSA
[4]. A Study on Data Storage Security Issues in Cloud Computing Naresh vurukonda1, B.Thirumala Rao2 1,2Department of CSE, KLUniversity, Vijayawada, A.P, INDIA 1 naresh.vurukonda@gamil.com, 2 drbtrao@kluniversity.in
[5]. “Security Guidance for Critical Areas of Focus in Cloud computing”, April 2009, presented by Cloud Security Alliance (CSA).
[6]. Arijit Ukil, Debasish Jana and Ajanta De Sarkar” A SECURITY FRAMEWORK IN CLOUD COMPUTING INFRASTRUCTURE “International Journal of Network Security & Its Applications (IJNSA), Vol.5, No.5, September 20l3 l0.5l2l/ijnsa.20l3.5502 ll.
[7]. Rabi Prasad Padhy, Manas Ranjan Patra and Suresh Chandra Satapathy ,” Cloud Computing: Security Issues and
Research Challenges”, IRACST – International Journal of Computer Science and Information Technology & Security
(IJCSITS) Vol. l, No.2, December 20l1.
