1Raksha Chouhan
1Faculty, Prestige Institute of Management and Research, Indore (Madhya Pradesh)
Abstract :- Internet based global fraud rate is increasing rapidly and there is a potential impact of cyber crime on quality production time, overhead cost, economy, market value as well as on consumer trust. Cyber space is used for violating copyright, trafficking in human organs and prohibited drugs, violating individual’s privacy, pornography, gambling, hacking, terrorism, money laundering, fraud, software piracy and corporate surveillance etc. Thus Growing danger from crimes committed against electronic information on computers is alerting us to claim attention in national capitals and dedicated legislation on cyber crime to supplement the Indian Penal Code is demand of the state of art. The objective of this research paper is to critically analyze cyber safety mechanism and trends to protect our society and to crack as to how the issue of cyber crimes has been dealt with in our society. This paper also examines the reasons behind failure of legal mechanism and also identifies the methods by which cyber crime can be reduced.
KEYWORDS: Cyber Attacks, Cyber Crimes, Cyber Law, I.T.A. 2000, ITAA 2008, Information Technology and National Security etc.
I. Introduction
Cybercrime is an activity performed by criminal by using an element of a computer or network of computers. According to an Assoc ham-Mahindra SSG study “The number of cyber crimes in the country may double to 3 lakh in 2015 and could pose serious economic and national security challenges” [4]. According to Computer Emergency Response Team-India (CERT-In) report till May 2014 total 9, 9,174 Indian websites were hacked by hacker groups spread across the world [5]. Methods of attack are becoming even more sophisticated with the passage of time. It has become one of the most serious economic and national security threats. It has affected almost every area including defense, medical, computer infrastructure, transportation, defense etc. Confidentiality, integrity with reference to quality, accuracy and relevance and availability are major role playing factors towards cyber security. A threat can be defined as a potential danger to information and system. Three levels of cyber threat have been shown below [1]:
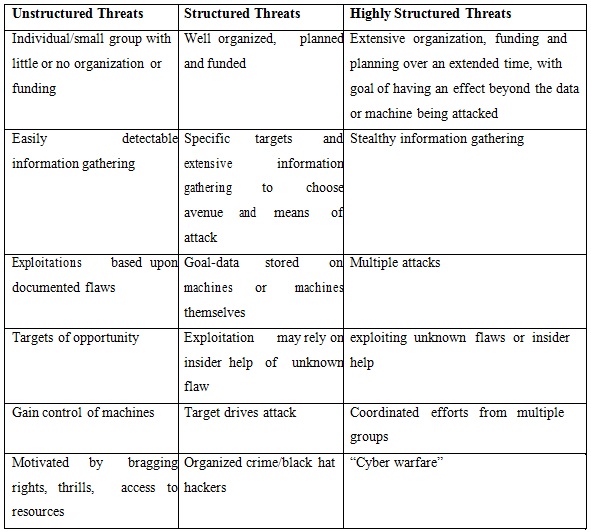
Table 1: Different Levels of Cyber Threat
Top-Ten Types of Information violated by hackers in 2013 are-Real Names, Birth Dates, Government ID Numbers (Social Security), Home Address, Medical Records, Phone Numbers, Financial Information, Email Addresses, User Names & Passwords and Insurance. Top-Ten Industries Targeted in Spear-Phishing Attacks in 2013 are Public Administration (Gov.), Services – Professional, Services Non-Traditional, Manufacturing Finance, Insurance & Real Estate, Transportation, Gas, Communications and Electric, Wholesale, Retail, Mining, Construction. In the following chart total number of vulnerabilities from 2006 to 2013 has been shown [2]:
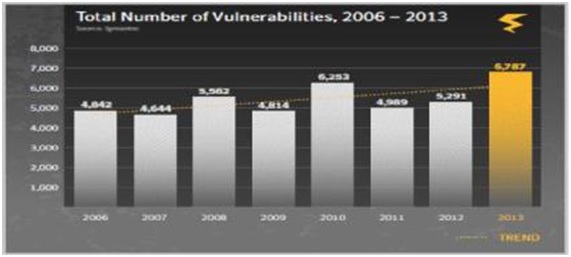
Fig 1: Total number of vulnerabilities from 2006 to 2013
Fig 2 is showing various stages of cyber attack evolution from year 1980 to the year 2000+ [3]:
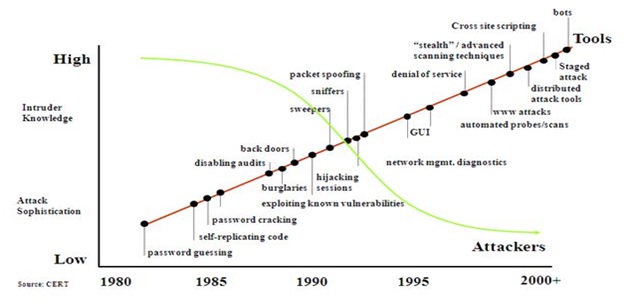
Fig 2: Various stages of cyber attack evolution
II. Objectives of the Study
- To critically analyze emerging trends for cyber safety mechanism to protect our society.
- To analyze the reasons behind failure of legal mechanism.
- To identify the methods by which cyber crime can be reduced for the betterment of the society.
- To find out various initiatives taken by international and national organizations towards cyber safety mechanism.
III. Methodology
All most every area like income tax, passport visa has been intensely involver in E-governance and now India is shifting gears towards E-governance. In this study a systematic review on cyber crime as well as upcoming trend used for cyber safety mechanism has been done. The study is focused on a safety mechanism and tries to identify, appraise, select and synthesize all high quality research evidence relevant to the matter. A combination of existing literature studies and in-depth secondary database material is used to fulfill the objective and the material has been referred from Online as well as desk based book reviews, articles, reports, research and conference papers.
IV. Most pervasive cyber crime schemes and reasons responsible for growth in cyber crime
Cyber Crime is on the increase and a lack of awareness, and inappropriate, limited or absent countermeasures have only aggravated the negative impact of e-fraud on society. Most pervasive cyber crime schemes are Internet auctions and retail schemes, Internet business opportunity schemes, Internet work-at-home schemes, Internet identity theft schemes, Internet investment schemes, Internet effortless income schemes, Internet free goods schemes, Internet health and diet schemes, Internet guaranteed loans or credit, on easy terms schemes, Internet credit repair schemes, Internet vacation prize promotions schemes, Internet ‘quick divorce’ scheme and Salami Techniques etc whereas reasons responsible for growth in cyber crime are[6]:
- 24X7 worldwide connectivity.
- Increasing complexity of computer software
- Availability of malicious code and tools in large quantity.
- Demanding pace of technological change.
- Slow adoption rate of good computer security practices
V. Counter Measures used to provide cyber safety mechanism
The most popular weapon in cyber terrorism is the use of computer viruses and worms. Antivirus stays helpless until and unless its database is updated periodically to discover new attacks like hijacking, Denial of Service etc. therefore other software’s are also needed along with the use of antivirus. It is good practice not to eliminate the firewall from our system even if it has limited capacities compared to IPS or IDS, because a firewall reduces the amount of the bad traffic that can reach the IPS and IDS, which will reduce the alarms and the suspicious data. Following are some Counter measures and cyber safety Mechanism used in current scenario [7] [8] [9]:
A. Intrusion Detection System (IDS): Any group of actions that attempt to compromise the integrity, confidentiality and availability of information is called as an intrusion. Hence Intrusion detection is considered as an additional wall to protect systems and it is useful not only in detecting successful intrusions, but also provides important information for timely countermeasures. Thus Intrusion Detection System is used to monitor events occurring in a computer system or network and analyzing these occurrences which may violate safety mechanism. The alarm of IDS is launched when an intrusion / interference have break in/enter the system. There are two types of IDS: HIDS and NIDS. HIDS is more reliable way as compare to NIDS because it can detect illegal access easily but at the same time HIDS delivers all the collected information to a central computer. This means that in an internal network if we have a big number of machines with HIDS then it may be risky because big flow of information could diminish the performance of the system, that’s why NIDS is preferred in that kind of network even that he could miss some illegal access that HIDS can see.
B. Intrusion Prevention System (IPS): We need something that prevents the attacks before it happens. IPS identifies and stops the malicious codes before they penetrate in our system; this type of software’s provides the 4‘h layer of protection shield to the system.
An intrusion detection and prevention system (IDPS) identifies possible incidents and their logging information, attempt to stop them, and generate a report to the security administrators. IDPS also used to identify problems with security policies and to documents existing threats. They use several response techniques, which involve the IDPS in stopping the attack itself, changes the security environment like by reconfiguring a firewall or changing the attack’s Content etc.
C. Distributed Intrusion Detection System (DIDS): DIDS are superset of the conventional IDS, implemented in a distributed environment. In DIDS, conventional IDS are fixed inside intelligent agents and are installed on a large network. In a distributed environment, IDS agents communicate with each other, or with a central server. Distributed monitoring allows early detection of planned and coordinated attacks and in this way allows network administrators to take preventive measures. DIDS also assists to control the spreading of worms, improves network monitoring, incident analysis, attack tracing etc. It also helps to detect new threats from unauthorized users, backdoor attackers and hackers to the network across geographically separated locations.
D. Agent Based Distributed Intrusion Detection System (ABDIDS): Agent based distributed Intrusion detection system is an essential factor of protective measures to protect computer systems and networks from exploitation. It is a fully distributed system and automates security management tasks. It is made by set of nodes with three types of agents: Monitoring Registry Agents (MoRA), Monitoring Agents (MoA) and managing agents (MA). Besides other functionalities of IDS it provides facilities like early warning when pre-attack activities are detected as well as detecting and isolating compromised nodes by trust mechanisms and voting-based peer-level protocols.
E. GPRS Security Architecture: GPRS uses a set of security mechanisms that comprises the GPRS security architecture. Most of these mechanisms have been originally designed for GSM, but they have been modified to adapt to the packet oriented traffic nature and the GPRS network components also. Two main goals of GPRS security architecture are to protect the network against unauthorized access, and to protect the privacy of users. Components of GPRS are Subscriber Identity Module (SIM), Subscriber identity confidentiality, Subscriber identity authentication and GPRS backbone security.
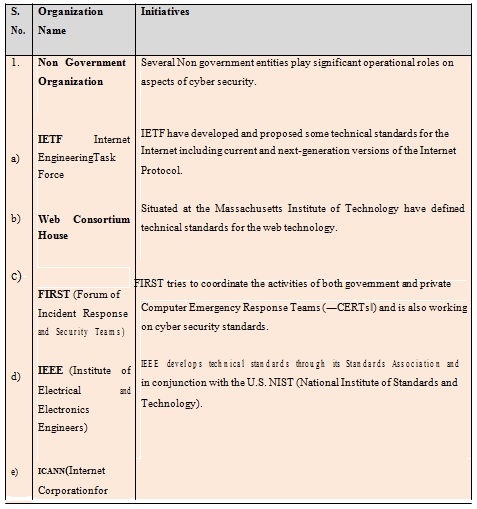
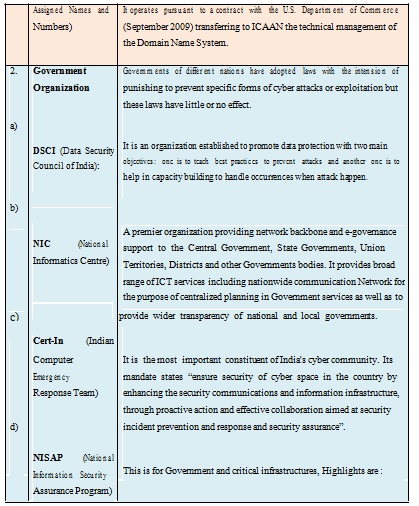
VI. Role of International / National Organizations towards Cyber Safety Mechanism
The economic growth of any nation and its security depends on how well is its cyberspace secured and protected. In recent cyber security measures Non Government (private) regulatory measures, National Law and enforcement measure, Defensive strategies, products as well as some limited forms of international cooperation and regulations plays important role. Some of the initiatives taken by private and government (national/International) organizations are shown in the following table [7] [10]-



VII. Conclusion
Online communication has become essential in digital age and as a result cyber crime has emerged as a very concrete threat. It is committed by technocrats and the returns are enormous and the risks are stumpy. In present scenario India is actually aware about its reputation because of the critical position of cybercrime where foreign investors can do business and has been investing heavily in cyber security.
One key to get better cyber security is an enhanced understanding of the threat and of the vectors used by the attacker to hijack important information. Implementation of a more methodological approach is required to freeze security. There are a variety of frameworks that can help, and each one may suit different organizations in different ways. Businesses and organization should adapt, use and maintain standard framework to fight with emerging threats and challenges. Some critical control protection priorities have been discussed below: [2]
- Unauthorized and unprotected system including servers, workstations, laptops etc connected to the enterprise network should be monitored and configured properly to avoid exploitation.
- Inventory should be maintained and only necessary and authorized software’s should be installed to reduce attacks.
- Easy access through networks and browsers should be prevented and Secure Hardware & Software Configurations should be deployed and regularly updated.
- Automated antivirus and anti-spyware software should be used to continuously monitor and protect workstations, servers, and mobile devices and they should be updated regularly and vulnerability should be repair quickly.
- Web application firewalls should be deployed to inspect all traffic, and errors should be checked explicitly for all user input (including by size and data type).
- Restoration process should be regularly tested and backup should be taken regular basis to minimize damages from an attack.
- Knowledge gaps should be identified properly and initiatives should be taken to fill these gaps by skillful training programs.
- Secure and standard Configurations for network devices such as Firewalls, Routers, and Switches should be used to prevent systems.
- Use of administrative licenses should be controlled to protect and validate an administrative account.
- Multi-layered boundary defense control should be established to control the flow of traffic.
Society as on today is happening more and more dependent upon technology and crime based on electronic offences are bound to increase. In the coming future new technology is going to provide broader opportunities for criminal by providing easier access to systems, premises, goods and information, and due to unlimited geographical coverage. The cost of cyber crime will continue to increase with the increasing functionality on internet of business organizations. The main challenge now for India is to train and equip its law enforcement agencies and judiciary, particularly outside big city like Delhi, Mumbai and Bangalore Government need to begin serious, methodical effort to collect and publish data on cyber crime so that countries and companies can make better choice for risk and policy.
References
- Amelia Muccio (April 13, 2011)”Introduction to Cyber security & Information Assurance for FQHCs” Director of Emergency Management, amuccio@njpca.org,visited on 17-3-15.
- Symantec Corporation, Internet Security Threat Report 2014:: Volume 19 2013 Trends, Volume 19, Published April 2014, PP 98, www.symantec.com.
- Lance James CTO, ( July 2005), “Phishing an evolution”, company confidential, secure science corporation Secure Science Corporation 7770 Regents Rd., Suite 113-535, San Diego, CA. 92122-1967, (877)570-0455, http://www.securescience.net.
- The Economic Times (Jan 5, 2015) “Cyber crimes in India likely to double to 3 lakh in 2015:Report”,http://articles.economictimes.indiatimes.com/2015-01-05/news/57705670_1_cyber-crimes-online-banking-pin-and-account-number.
- Computer Emergency Response Team-India (CERT-In) reports 62,189 cyber attacks till May 2014, http://www.techmistory.com/2014/07/cert-in-reports-62189-cyber-attacks.html, visited: 10-1-15.
- Dr Hugh McDermott (visited: 24-1-15), Cyber Crime – Present and Future Trends Director, AML-CTF, Fraud & Financial Crime Program, Australian Graduate School of Policing, Charles Strut University, pp 52.
- Atul M. Tonge, Suraj S. Kasture , Surbhi R. Chaudhari(2013), “Cyber security: challenges for society- literature review”, IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278- www.iosrjournals.org.
- Janhavi J Deshmukh and Surbhi R Chaudhari (April’ 2014), Cyber crime in Indian scenario – a literature snapshot, International Journal of Conceptions on Computing and Information Technology, Vol.2, Issue 2, pp 24-29, ISSN: 2345 – 9808.
- Baroudi Siba, Ziade Haissam, Mounla Bassem (2004), “Are we really protected against hackers?” Proceddings International Conference on Information and Communication Technologies: from theory to application. PP. 621-622. IEEE
- Col S S Raghav (visited: 28-11-14), “cyber security in india’s counter terrorism strategy”, pp 5, ids.nic.in.
